
Andrew Ginter’s Top 3 Webinars of 2024
Get up to speed on key trends and strategies in industrial security with Andrew Ginter’s favorite webinars of 2024,
Welcome to the resources page! We have compiled a collection of useful information, tools, and resources to help you

Get up to speed on key trends and strategies in industrial security with Andrew Ginter’s favorite webinars of 2024,

Sit back and enjoy Andrew Ginter’s top 3 picks from 2024’s Industrial Security Podcast series.

Spoiler Alert: Yes, investing in OT security is very much “worth it”. It helps prevent financial losses, operational disruptions, and compliance penalties far exceeding initial costs. The average ROI can reach up to 400%, ensuring both protection and operational continuity.
I recently had opportunity to ask experts @Marc Sachs, @Sarah Fluchs and @Aaron Crow about their experience with the new Cyber-Informed Engineering (CIE) initiative.

Upstream Oil & Gas production has a unique range of threats and risks to consider when compared to other industrial operations.
Our checklist infographic takes a dive into what to consider and secure when it comes to Upstream operations.

IT/OT integration introduces threats to reliable operations. Connected networks move both data, malware, and remote-control cyber attacks along their wires and cables. In the Oil & Gas industry, E&P, pipelines, and refineries have found that securing IT/OT connections involves more than just having Enterprise Security telling Engineering what to do and Engineering saying “no” to IT over and over.
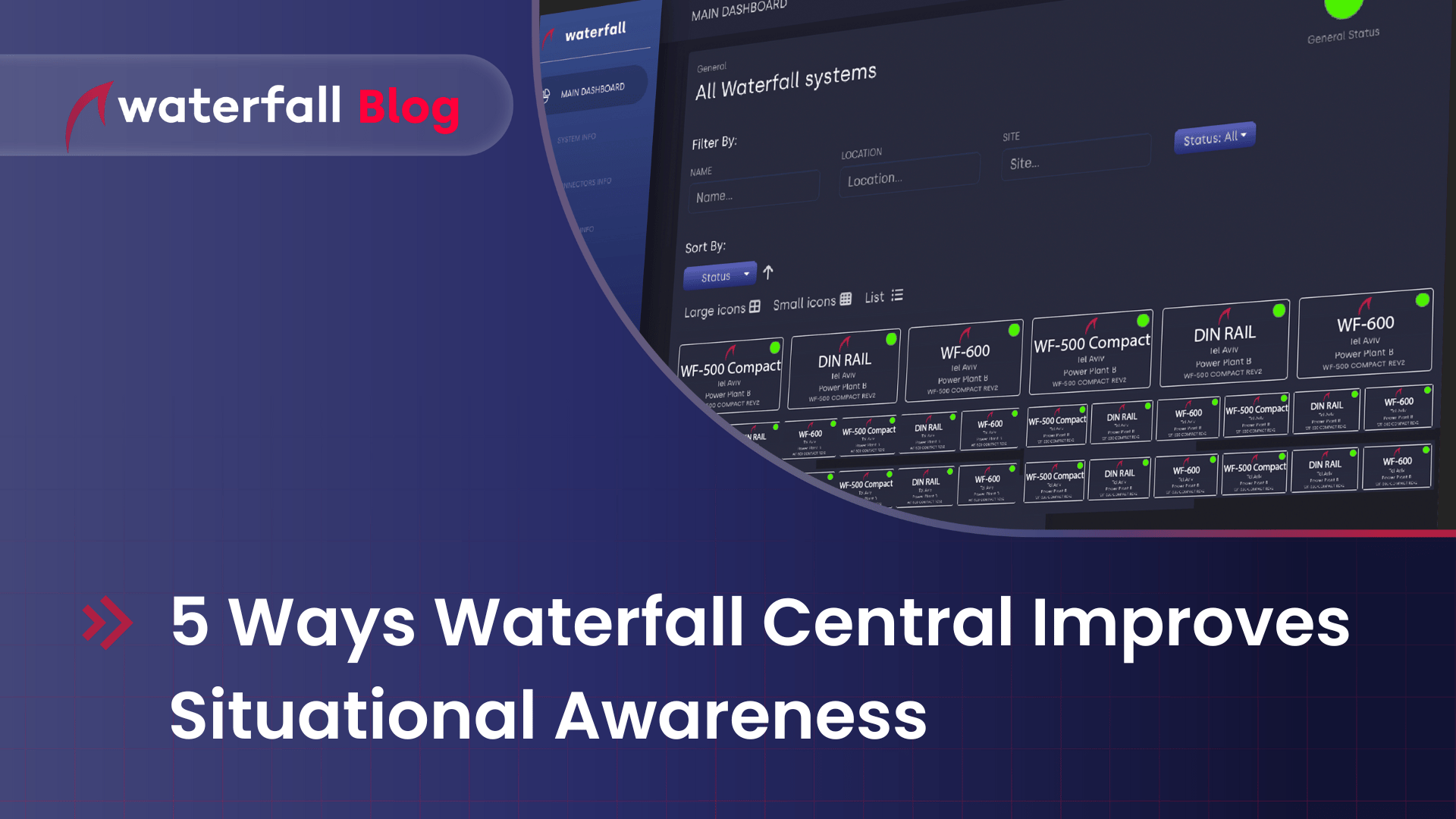
Introducing Waterfall Central: Come for simple remote monitoring of multiple devices, stay for operational awareness.
Waterfall is proud to be recognized by Amazon as a validated industry standard for connecting OT systems to the AWS Cloud.

Andrew Ginter shares with us his top 5 favorite podcast episodes from the Industrial Security Podcast that he co-hosts
Managing OT Cyber risk takes on different approaches and expertise depending on the potential consequences of compromise to a particular system. This is why it is important to delve into the distinction and importance of an engineering-centric approach to managing OT cyber risk.