Unbreachable Access to OT Data
Unidirectional Gateways deliver unbreakable protection for OT environments while ensuring secure, continuous access to critical OT data without compromise.
Cyber Physical Protection
Absolute Protection
Gateway hardware ensures one-way data flow, preventing any inbound threat.
Network Visibility
Seamless access to OT network servers through replicated date on the enterprise network.
Uninterrupted Performance
Redundant power supplies and network interfaces ensure uninterrupted operation, even if a component fails.
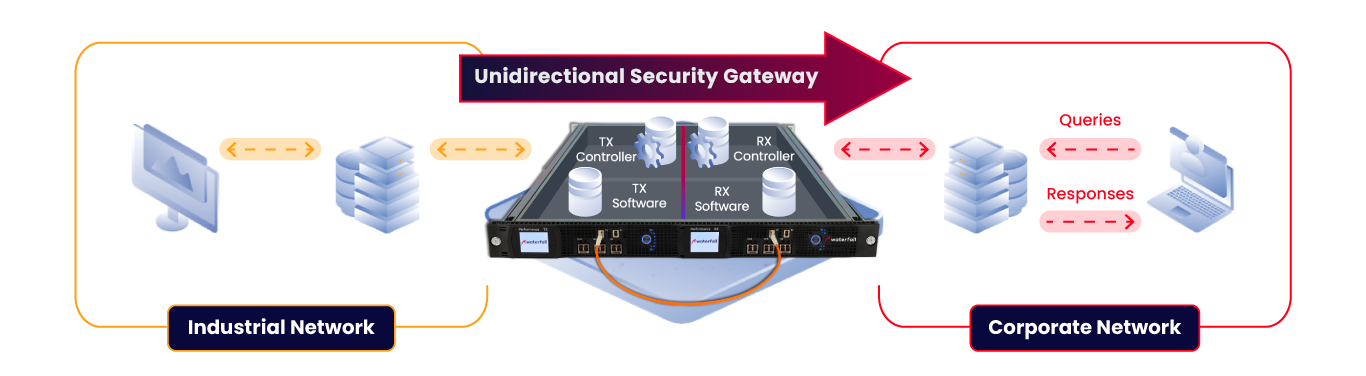
Unidirectional Protection in Action
Unbeatable security with seamless enterprise connectivity
Connect
Set up the unidirectional gateway on your network to ensure data only flows in one direction to your IT network.
Replicate
Collect data from your OT servers and replicate it on your enterprise network without compromising security.
Access
Enable users to securely access the replicas while keeping your industrial network protected from any incoming threats.
Use Cases

How can I comply with OT / industrial security standards and regulations?
Discover how
How can I protect my OT networks from ransomware?
Discover how
How can I keep my facilities out of the news?
Discover how
How can I connect my OT data to the cloud, safely?
Discover how
How can I make my forensic records tamper-proof?
Discover howSecurity First Design
Prioritizing cybersecurity in every aspect. Hardware-enforced security at the site perimeter – No cyber attack can get through the unidirectional hardware to put physical operations at risk.
Strong physical segmentation – Data queries and responses occur exclusively within the IT network, without ever passing into OT environments.
Strong Physical Segmentation
Data queries and responses occur exclusively within the IT network, without ever passing into OT environments.
Universal Data Access
Compatible with Waterfall’s large library of off-the-shelf connectors for a wide array of OT and even IT data sources, servers and protocols.
Scalable Performance
Choose between 1Gbps or 10Gbps throughput options to meet the demands of your site and ensure seamless data processing.
All-in-One Performance
A fully integrated solution requiring no additional hosts or software installation within your OT or IT networks, simplifying deployment and management.
Easy to Use
The web-based user interface is the sole interface you’ll need, enabling you to configure, manage, monitor, and troubleshoot with ease.
Battle Proven
Already deployed at thousands of sites worldwide, demonstrating proven reliability and performance.