The Network and Information Systems Directive (NIS2) primarily focuses on information technology (IT) and addresses the protection of Internet infrastructures like DNS servers. It does not explicitly mention Operational Technologies (OT) and even categorizes sectors so disparate as energy and banking as equally as critical. NIS2 and its impact can leave OT professionals scratching their heads on how NIS2 affects them.
There is ample information about NIS2 available, and the directive itself can be read here on the European Union’s website. The English version stands at 72 pages, 46 articles, and 3 annexes, and is a great read for those having trouble sleeping. The key takeaway for highly critical OT environments, such as energy, transport, and water management, is that NIS2 establishes a set of rules and minimum requirements to foster EU-wide cooperation and reporting.
Compliance with NIS2 regulations does not guarantee protection against external cyberattacks. The regulations aim to mitigate risks and ensure that operators of essential services and digital service providers take some measures to secure their networks. However, these minimum measures may be inadequate for OT systems, where the impact of a cyberattack could be truly unacceptable.
Beyond the basics, Article 21 of NIS2 states that entities “shall ensure a level of security of network and information systems appropriate to the risks posed.” In this context, we will now examine how NIS2 should be applied to OT systems according to standard focus texts, such as the upcoming Network Security Codes for Electricity in Europe, and what this means for compliance.
NIS2 Basics
After a two-year legislative process, the European Parliament reached a consensus on the updated NIS2 in May 2022. NIS2 replaces the NIS Directive (NISD) enacted in 2016, but the impact on operational technology (OT) security remains unclear. Affected OT sectors include energy, transport, healthcare, drinking water, wastewater, ground installation serving space-based services, and manufacturing (for mid-sized companies and larger).
But why was NISD replaced by NIS2? There are several factors. In my opinion, these are the most important:
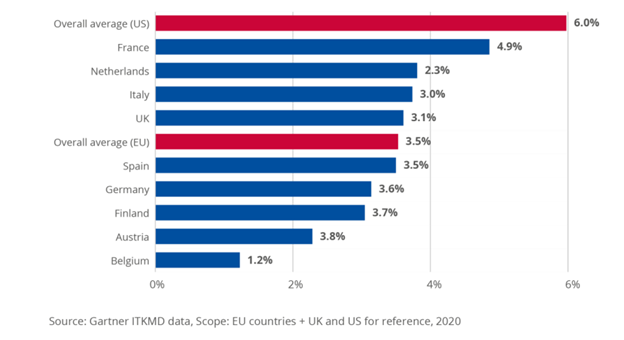
- Poor cybersecurity investment in the EU: A 2020 study by ENISA found that EU organizations allocate 41% less to information security than their US counterparts, despite having NISD in place for four years.
- Lack of clarity in NIS: In the same study, 35% of respondents applying NIS reported unclear expectations, leading to inconsistent application across EU states.
- Increase in cyberattacks: Ransomware and other cyberattacks have affected EU infrastructure, with some infrastructures lacking basic protections such as segmentation of the IT/OT interface.
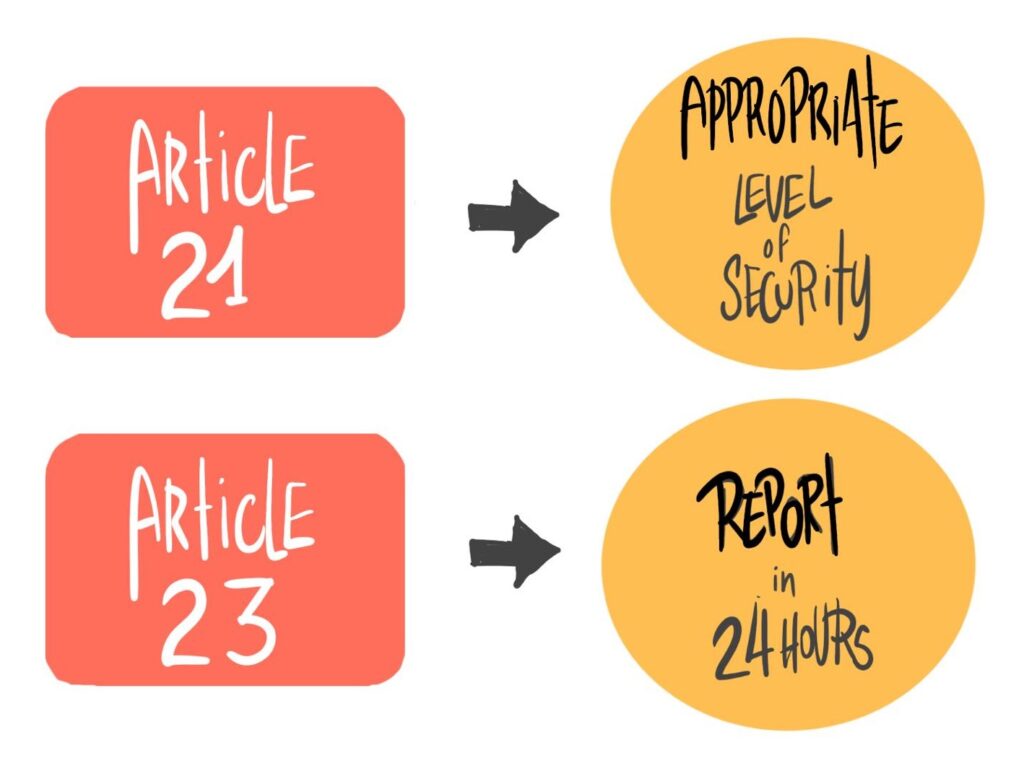
Articles 21 and 23 are the two primary articles in the NIS2 Directive for OT professionals to act upon. Article 21 addresses the management of cyber risk, while Article 23 pertains to reporting. The NIS2 Directive specifically outlines the penalties for non-compliance with these two articles: The maximum fine is either €10,000,000 or 2% of the entity’s global annual turnover from the previous financial year, whichever amount is greater.
The Meat for Operators: Articles 21 and 23
Understanding how Article 21 will be implemented in OT networks is crucial. Article 21 states that, taking into account the state-of-the-art and relevant European and international standards, organizations must ensure a level of security for network and information systems appropriate to the risks posed. This is further specified in Article 25, which encourages the use of European or international standards.
To address the “appropriate” wording in the legislation regarding cybersecurity requirements, asset owners in these industries should prioritize addressing cybersecurity issues present in their OT networks. This need does not apply in many other sectors covered by the NIS Directive, where the primary concern remains the vulnerability of Information Technology (IT) systems. However, upcoming standards and legislation will focus on OT networks, and the wording of NIS2 (which states that protection of assets should match the risks) points in that direction. In this blog, we will explain how the current Network Codes for Cyber Security (NCCS) for electricity illustrate this point.
For mid-sized manufacturing or healthcare sectors, Article 21 will have a significant impact, as cybersecurity standards in these sectors are relatively low and owners and operators in these sectors know that they will be labeled as essential and highly critical. As such affected organizations will need to develop cybersecurity policies to comply with the directive.
Article 23 discusses reporting. Organizations must report any cyber incidents quickly – an early warning must be issued within 24 hours, followed by an incident notification within 72 hours, and a complete incident report within one month.
Additionally, operators should collaborate with established national and EU-wide organizations. EU member states will create national organizations like Computer Security Incident Response Teams (CSIRTs) to supervise the adoption of the directive. These organizations will report to pan-European bodies such as the European Cyber Crisis Liaison Organization Network (EU-CyCLONe).
NCSS: An example of Implementing Article 21 for Operators
For OT operators in critical infrastructure sectors such as energy or transportation, more focused standards and directives should be considered to comply with article 21, such as the upcoming Network Codes on sector-specific rules for cybersecurity aspects of cross border electricity flows (NCCS) or sector-specific standards such as TS-50701 for rail systems. and its likely standard successor IEC63452. NIS2 focuses on reporting, creating agencies, and imposing fines for non-compliance. As consequences become more severe, so should the cybersecurity measures utilized.
The Network Code on Cybersecurity aims to establish a unified European standard for safeguarding cross-border electricity flows’ cybersecurity. This code includes regulations on assessing cyber risks, implementing shared minimum requirements, certifying cybersecurity for products and services, monitoring, reporting, and managing crises.
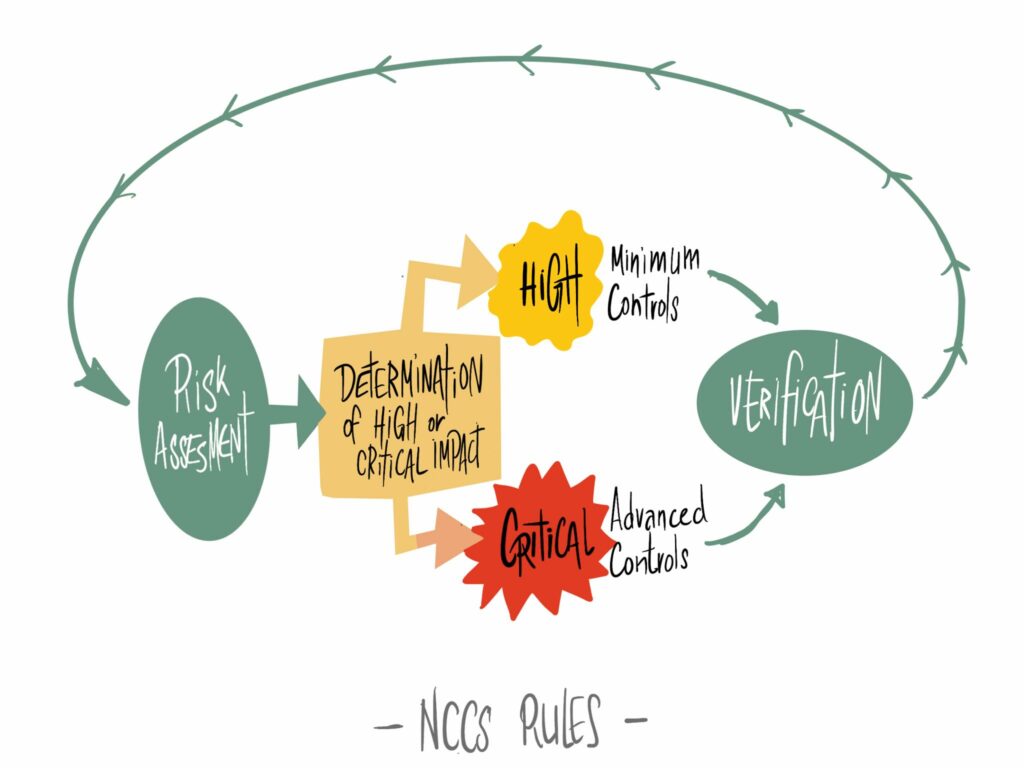
The NCCS approach to cybersecurity involves establishing both high-impact and critical-impact perimeters based on the Electricity Cybersecurity Impact Index (ECII). This methodology is likely to categorize systems according to business consequences and reliability/safety consequences.
The minimum cybersecurity controls should be applied to both perimeters, while the critical-impact perimeter should be protected with advanced cybersecurity controls. This requires a strict separation between critical and non-critical impact perimeters, potentially at the IT/OT interface, and utilizing advanced perimeter solutions, including physical segmentation such as unidirectional security gateways. In addition, the minimum and advanced cybersecurity controls and the electricity controls to standards mapping Matrix (ECSMM) will map controls to a selected set of international standards, such as IEC62443. The consequences of cybersecurity attacks must be considered for risk assessment as required by NIS2. These consequences include loss of load, reduction of power generation, loss of capacity in the primary frequency reserve, and loss of capacity for a black start.
Conclusions
NIS2 holds significant implications for OT professionals, especially in critical infrastructure sectors. Although the directive’s emphasis on IT systems might cause some confusion, it is crucial for OT professionals to familiarize themselves with the key articles, create strong cybersecurity policies, and collaborate with relevant government organizations to ensure compliance and reduce risks. As stated in Article 21 of NIS2, risk assessments should be consequence-driven and geared towards more focused cybersecurity standards by sector, such as the Electricity Network Codes, which indicate a strict separation between high-impact and critical-impact areas. This approach is reflected in other recent standards as well, such as TS-50701 for railway networks. Given the emphasis on reporting and consequence-based risk assessments, OT operators in critical sectors like energy, transportation, and water, as well as medium-sized and larger manufacturing companies, should begin strictly segmenting their networks by impact to avoid fines in the event of an incident.
Learn more about how to comply with the recent NIS2 regulation
