The 2024 Threat Report – At a Glance
Cyber attacks impacting physical operations, like shut-downs, are rising. Waterfall’s NEW annual threat report provides industrial operators with the latest trends in the threat environment to prepare themselves going forward.
Rees Machtemes, P.Eng.

Forewarned is Forearmed
Attacks with physical OT consequences increased in 2023. Attacks increased to 68. Impacted OT sites increased to over 500. Hacktivists and nation states are targeting and impacting critical infrastructures. Supply chain impacts are back. These new insights from the new 2024 Threat Report are available in a collaboration between Waterfall Security Solutions and ISSSource. The collaboration reports on credible public disclosures of cyber attacks with physical consequences in world-wide discrete manufacturing, process, and critical industrial infrastructure industries. As it is every year, this report is designed to be the most credible and conservative report available to OT/ICS cybersecurity practitioners, to best advise and assist industrial operators to mitigate threats in their field.
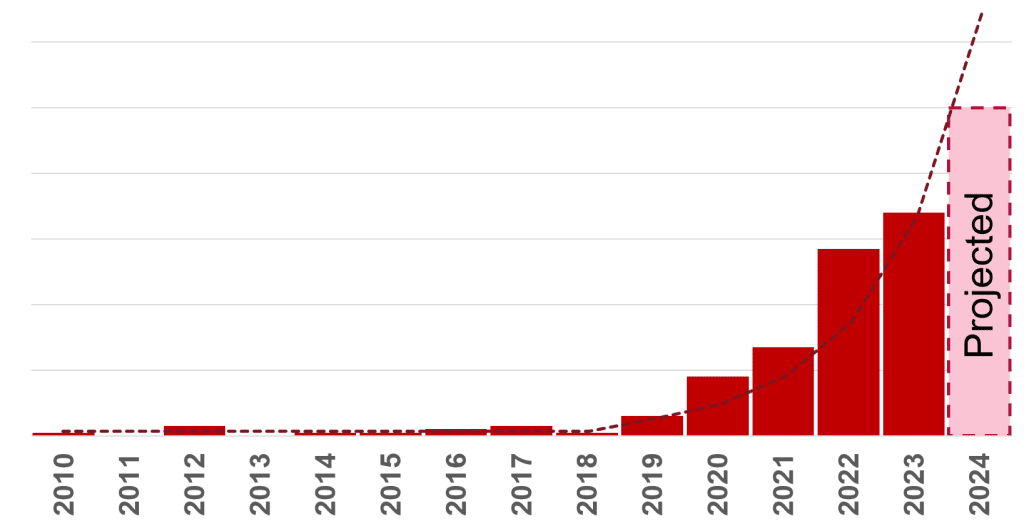
The report covers all cyber attacks, that meet our inclusion criteria, from 2010 to 2023’s year-end. The report shows that in the past decade (from 2010 to 2019), OT cyber threats were a largely theoretical problem. However, in this decade (2020 to present), the problem has become very real and these kinds of attacks are nearly doubling annually at exponential growth. At the current rate, we should expect to see 100 cyber attacks by this year’s end (2024) to cause shut-downs or other physical consequences in hundreds of industrial sites world-wide.
The joint Waterfall and ISSSource 2024 Threat Report covers year-on-year attack trends to see where we are headed in the global cyber threat environment.
Big Impacts & Major Findings
 The report’s data-set shows that ransomware is responsible for 80% of attacks in 2023 where the attack type could be attributed, impacting physical operations all over the world. A minority (15%) of attacks were due to hacktivists – “amateur” attackers with a political agenda. All of the year’s hacktivist attacks with physical consequences were associated with two on-going physical conflicts: The Iran-Israel proxy conflict and the Russo-Ukrainian War. These attacks brought about not just physical shutdowns but also large financial losses. High-profile incidents and trends in 2023 include:
The report’s data-set shows that ransomware is responsible for 80% of attacks in 2023 where the attack type could be attributed, impacting physical operations all over the world. A minority (15%) of attacks were due to hacktivists – “amateur” attackers with a political agenda. All of the year’s hacktivist attacks with physical consequences were associated with two on-going physical conflicts: The Iran-Israel proxy conflict and the Russo-Ukrainian War. These attacks brought about not just physical shutdowns but also large financial losses. High-profile incidents and trends in 2023 include:
- Over half (54%) of incidents impacted discrete or process manufacturers, in sub-industries such as electronics, automotive, marine, cosmetics, and metals.
- Numerous hacktivist attacks targeted Israeli-manufactured Unitronics Vision controllers deployed at water utilities worldwide.
- Cyberattacks caused logistical outages and delays at five sea ports in Australia and Japan.
- There were eleven (11) incidents where the victim organizations made financial disclosures or reports to the US SEC, London Stock Exchange (LSE), and other authorities,
- Two (2) novel supply chain attacks had malicious firmware code inserted into the victim’s devices that subsequently impaired operations.
- One of these attacks was cited as causing bankruptcy and mass-layoffs, adding to two similar incidents in 2022.
New insights this year stem from a detailed analysis of how attacks impair physical operations. Every incident going back to 2010 was rated by attack type, examined as to how the attack either directly or indirectly impacted the OT network or asset. 25% of attacks impacted OT networks and systems directly, and the remainder impacted operations only indirectly, but still had physical impacts.
Ransomware tactics and motivations evolved in 2023. Some ransomware groups appear to be shifting tactics to “data exfiltration only,” by stealing information without encrypting it. This is likely a factor behind a slightly slower growth in consequential OT incidents this year than in last year’s 2023 Threat Report. Also, Microsoft and SentinelLABS report that both nation-state and ransomware threat actors are now synergistically leveraging each other’s malware code and tools. I.e. not only are ransomware groups employing nation-state-grade tools and techniques, but nation-states are taking ransomware tools and re-purposing them for their own attacks.
Good News
The new report also highlights defensive developments in the year 2023. Hot on the heels of last year’s Cyber-Informed Engineering Strategy the US DOE & INL in September published their Cyber-Informed Engineering Implementation Guide. More of a strategy book full of questions to ponder than a “How-to” instructional manual, the Implementation Guide never-the-less is the most important development in cybersecurity since the term “OT Security” was coined in 2005. The ultimate goal of the CIE CIE strategy is to both teach cybersecurity to engineers, and to bring powerful engineering tools to cybersecurity – tools that do not exist in ISO 27001, the NIST CSF 2.0, IEC 62443 or any other cybersecurity standards.
Bottom Line
The joint Waterfall and ISSSource 2024 Threat Report covers year-on-year attack trends to see where we are headed in the global cyber threat environment. To the greatest extent practical, the team behind the report has gathered as much data as publicly available to track the number and frequency of these cyber events. The complete data set for the report is included in an appendix, complete with links to public reports of the attacks. The report also covers important defensive developments, including the CIE, as well as developments in artificial intelligence and global standards and guidelines.
About the author
Rees Machtemes, P.Eng.
Share
Trending posts
Stay up to date
Subscribe to our blog and receive insights straight to your inbox