Refineries are some of the safest production facilities in the world. Oil and gas industries practice some of the strictest workplace safety and security of any industry. A serious malfunction at a refinery not only threatens human lives and the environment, but unplanned shutdowns at this type of critical infrastructure are extremely expensive and can have impacts on public safety. In this very strict, consequential environment, industrial oil and gas cyber security is increasingly a problem.
Industrial cyber security is a factor because efficient refining operations demand automation – both process automation and IT-style business automation. To enable that automation and digitalization, IT systems and operations technology (OT) systems are increasingly connected, both within their own networks and across the so-called IT/OT interface. This is a problem, because all cyber sabotage attacks are information and every communications channel that lets information move across networks also lets in cyber attacks. Ever-increasing connectivity deployed in support of steadily-increasing automation results in an every-increasing number of attack vectors that put digitized refineries at risk.
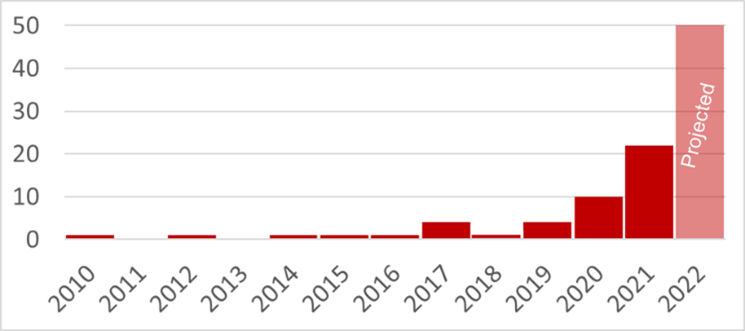
Attacks on oil and gas cyber security show no signs of slowing down
Cyber attacks that cause production outages or other physical consequences were a largely theoretical problem a decade ago. Over the past 5 years, however, such attacks are growing exponentially in sophistication, malintent and ubiquity. The 2017 TRITON attack that compromised Safety Instrumented Systems (SIS) in a Middle Eastern petrochemical facility and twice shut down the facility, shows that this cyber threat is very relevant to the refining industry. The increase in industrial exploits is evidence that connecting enterprise networks to ICS networks can open attack vectors for bad actors to spread malware and even to issue malicious commands deep into control system devices.
Worst-case consequences drive cyber security requirements
The modern approach to dealing with cyber threats due to connectivity starts with identifying both networks at differing levels of criticality and “criticality boundaries” – connections between networks whose worst-case consequences of compromise differ sharply. Determining this consequence delta is the sweet spot to properly defending operational technology.
At most refineries, the most important criticality boundary is between the enterprise network and the plant-wide Process Control Network (PCN). Worst-case consequences of compromise on the enterprise network include the potential for lawsuits, reputational damage and other negative repercussions of breaches of personally-identifiable information (PII), as well as clean-up costs: identifying, isolating, erasing, and restoring compromised equipment from backups. Worst-case consequences of cyber compromise on PCN networks include costly production downtime or possibility of fires, explosions, worker casualties and even threats to public safety. These are sharply and qualitatively different kinds of consequences – we cannot restore lost production, the environment or human lives “from backups.”
Engineering Cyber Security Approach – Unidirectional Security Gateways
In response to both the deteriorating threat environment and the need to keep safety as a top priority, many refineries are investing in unbreachable unidirectional protection at this critical IT/OT boundary. What does this look like? Unidirectional Gateways eliminate targeted ransomware and other modern threats because the gateways physically send information in only one direction: from the PCN network out to business automation. A fiber-optic transmitter in the PCN side of the gateway sends information to a receiver on the enterprise side. The receiving circuit board contains no transmitter or laser. This makes the receiving hardware physically unable to send any information back to the transmitter. If all information is prevented from flowing back through the hardware to the protected PCN network, then no attacks can flow back either – the unidirectional hardware is physical protection from cyber attacks.
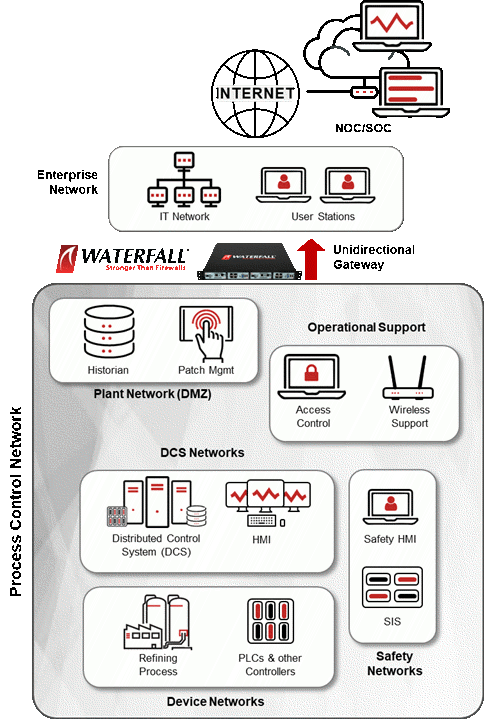
Whereas enterprise-grade defenses are probabilistic – meaning they may or may not defeat attacks depending on several external variables – Waterfall Unidirectional Security Gateways are deterministic protection. The gateways prevent all remote attacks from entering the protected network, no matter how sophisticated that ransomware, malware or other cyber attacks might be today or might become in the future. Deterministic solutions are engineered for a safety-minded environment – they provide the same degree of reliable protection, consistently.
Security Is Essential to Safety
Maintaining the highest level of engineering-grade industrial cyber security at refineries is essential to maintaining safety standards. Beyond safety, refining is critical infrastructure, and costly downtime and unplanned shutdowns carry enormous financial and societal costs. Preventing cyber attacks on operational networks at petrochemical facilities is key to maintaining safe and reliable operations for all stakeholders.
When we control the flow of information at criticality boundaries with physical, unidirectional hardware, we control the flow of attacks. Unidirectional Gateways are engineering-grade solutions to connectivity risks at criticality boundaries.
Reading Further on Oil and Gas Cyber Security
To dive deeper into use cases, strategies, and solutions for cyber security for refining, please download Waterfall’s guide: Cybersecurity for Refining. The guide explains how refineries can achieve deterministic, unbreachable protection for safe and reliable operations, while continuing to enjoy the efficiency, optimization and real-time OT visibility benefits that come from modern business automation.
