Unbreachable OT security,
unlimited OT connectivity
Waterfall provides unbreachable security solutions that keep the world’s most important industries and infrastructures running. Our innovative IT/OT integration technology guarantees safe, secure, and reliable operations, protecting against both today’s cybersecurity challenges and those yet to come.

Unbreachable
Our solutions are unbreachable, providing OT networks with safe IT/OT integration and 100% protection against cyber attacks.

Unlimited
Our innovative products eliminate remote network threats while enabling enterprise-wide visibility into physical operations.

Proven
For over 15 years, Waterfall's solutions have been trusted by all types of critical industrial infrastructures and are deployed at thousands of sites worldwide.

Innovative
Waterfall invented Unidirectional Gateways and we continue to innovate. Our mission is to revolutionize how entire industries protect physical assets and industrial processes from cyber attacks.
Who we protect
Cybersecurity for power plants
Power utilities rest easy knowing that remote cyber attacks cannot reach through their Unidirectional Gateways to mis-operate control systems responsible for worker and public safety, for preventing damage to long-lead time turbines and other equipment, or for assuring continuous and efficient production of electric power.

Cybersecurity for oil & gas
Owners and operators of offshore platforms, pipelines and refineries rest easy knowing that no cyber-sabotage attack is able to penetrate Unidirectional Gateway hardware to put at risk worker or public safety, the environment, long-lead-time equipment and reliable production and operation, without unplanned shutdowns.
Cybersecurity for rails
Rail and metro system operators rest assured when Unidirectional Gateways are deployed to protect vital networks including switching systems, electric power systems and operations control centers from cyber attacks originating on IT or Internet networks, no matter how sophisticated such attacks are now, or might become in the future.

Cybersecurity for facilities
Data centers, airports, government and military campuses and other very important facilities operators sleep well knowing that Unidirectional Gateways are unbreachable in the face of attacks traversing Internet-exposed IT networks to put public safety, important equipment and continuous & connect operations at risk
Cybersecurity for water Treatment
With Unidirectional Gateways deployed, municipal leaders can be confident of continuous and correct operation of their automation systems and water treatment infrastructure , even in the face of the most sophisticated of attacks coming across the Internet, both today and long into the future.
Cybersecurity for manufacturing
Nobody wants to be in next week's headlines explaining how another dozen plants were taken down by ransomware or other cyber attacks. Neither ransomware nor the most sophisticated of the Internet's attacks can breach Waterfall's Unidirectional Gateways to pose any threat to product quality or to continuous, and correct manufacturing operations,

How can I comply with OT / industrial security standards and regulations?
Discover how
How can I protect my OT networks from ransomware?
Discover how
How can I keep my facilities out of the news?
Discover how
How can I connect my OT data to the cloud, safely?
Discover how
How can I make my forensic records tamper-proof?
Discover howWhy Waterfall
Unidirectional Technology Is Recommended
By Standards Organizations Worldwide




















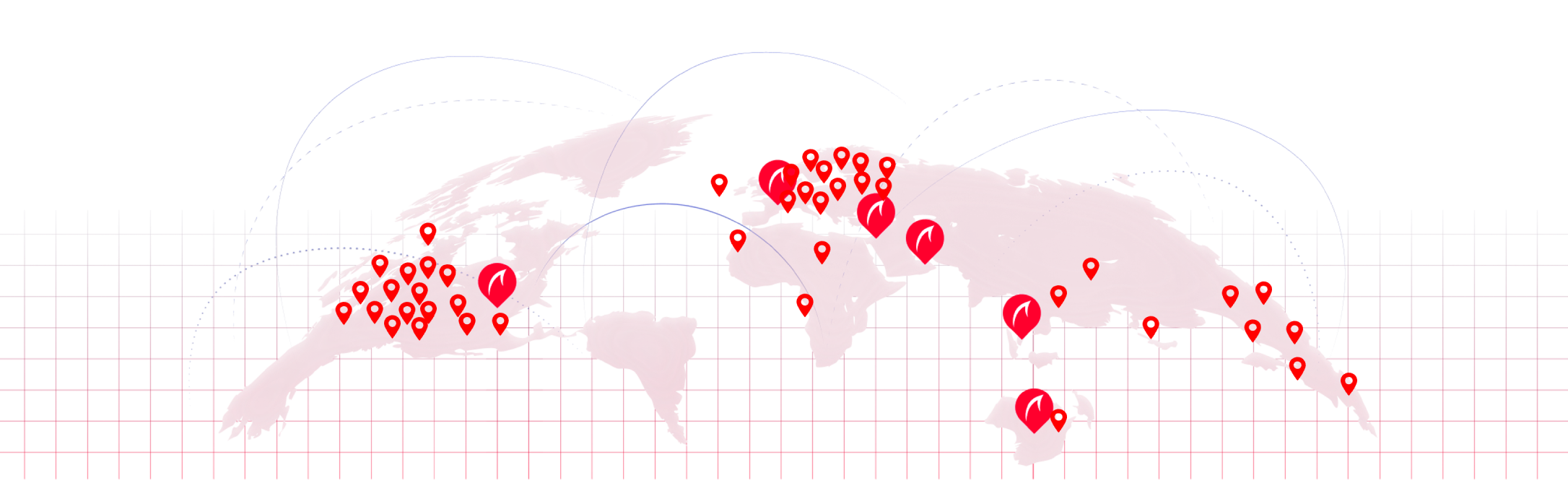
Thousands of sites globally

2007
Founded

>1000
Sites
>20
Verticals

6
Global Sales & Ops Hubs

14
Published Patents






