Protecting Water Utilities and Wastewater Treatment Plants

Mariano Martin Tirado
Tech Leader at Accianoa S. A.
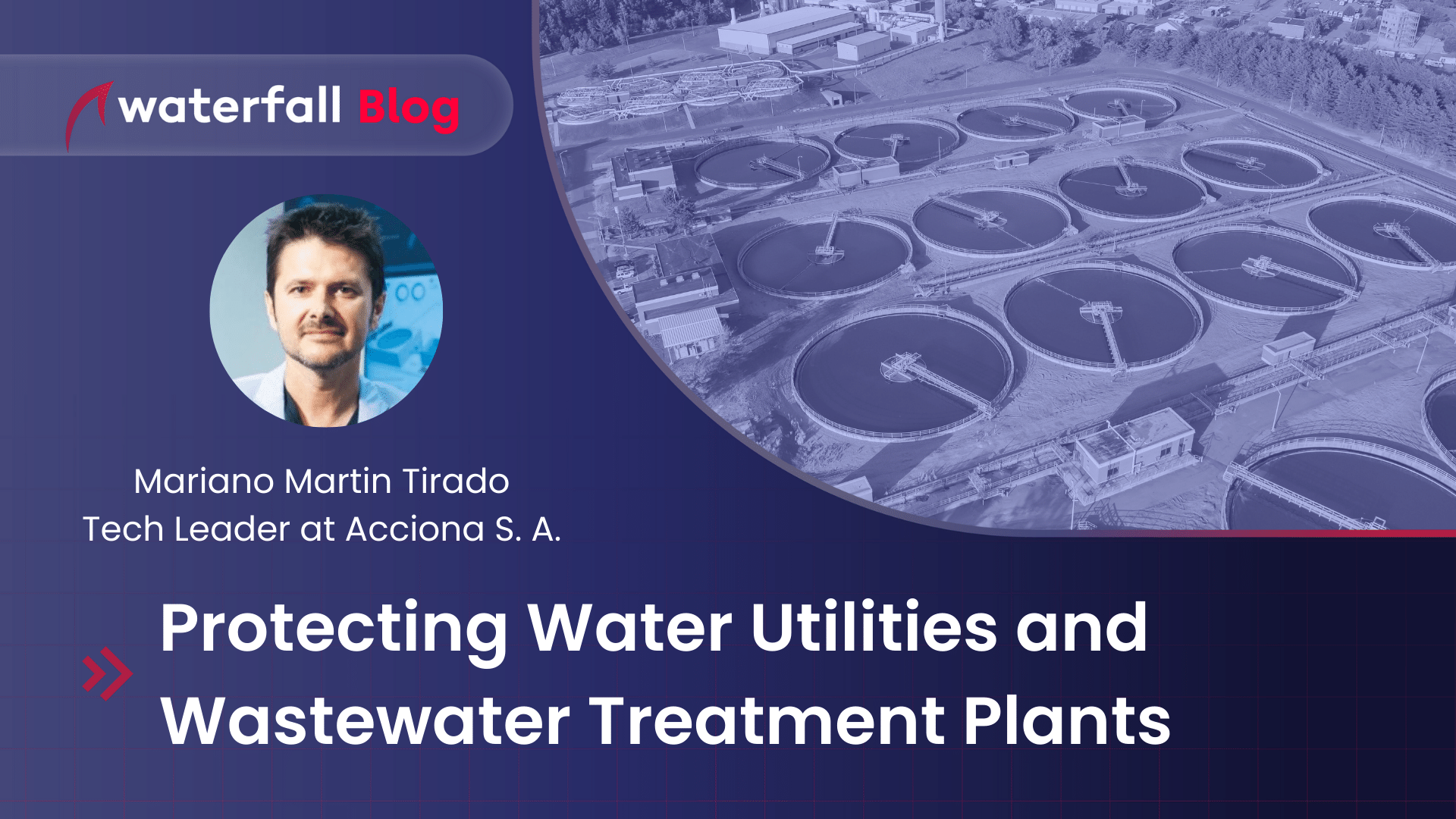
The first problem with securing water facilities is that many were built over 20 years ago. None of the common security protocols are in place. No firewalls, no passwords, nothing to prevent cyberattacks. And the reason for this problem is because such capabilities and threats didn’t exist when the water facility was first installed decades ago. So that is the first issue that needs to often be dealt with.
Water utility clients are naturally very concerned about cybersecurity attacks because you only have to watch the news to see the threats cyberattacks pose to water facilities around the world. Nowadays, cyberattacks that try to target these types of facilities do so because of their strategic/critical importance. The attacker’s motivation isn’t for money usually, but rather for clout and bragging rights. There is also a common concern that unfriendly governments will target such facilities as a strategic threat, as well as the common threat of ransomware.
“The first problem with securing water facilities is that many were built over 20 years ago.”
Cyber Threats of Water Utilities
When someone attempts to maliciously access water facilities, there are two main types of motivations. One of them is to SHUTDOWN the facility with the goal of making it not possible to start up again. In water starved areas, this can be a very big problem. The second possible motivation is that someone may try to change the mixing and chemical makeup of the water such as adding too much chlorine, lye, or any other chemicals which can cause a problem to the health of those bathing or drinking the water.
The control systems that run these water systems have many alarms and warnings to make sure the chemicals are within the approved parameters, but if someone takes control of the control systems, they would be able to deactivate these alarms. Manually tested samples are taken from the water too, but usually this is done once a day -not constantly like the automated censors. It could be that the tainted water has already entered the main supply by the time it gets manually tested.
Risks for Wastewater Treatment Plants
Attacks on the wastewater systems are also a big concern. Imagine a big city with the entire wastewater and sewage system not running. It would become a very unpleasant problem very quickly. The motivations and risks from an attack on wastewater systems are similar to an attack on regular water utilities. Concerns are also similar, with the risk of someone breaking or shutting down the wastewater systems, or someone messing with the controls so that sewage is not treated properly, also impacting the health of the people when it is released into the environment.
Water and wastewater are physically separated so that a hacker can’t mix the two, but the wastewater that can’t be treated because of a cyberattack needs to be released by the bypass which then damages the rivers and streams that it is released into.
IT and OT in Water Utilities
The billing of the water facilities is part of the IT system and is kept fully separated from the OT network that ensures the water supply. It is impossible to jump from IT to OT and OT to IT when the systems are properly isolated.
Part of a Supply Chain Attack
There is also a concern of a supply chain attack of someone attacking the electrical systems powering the water utility. With wastewater it is important to not require external power to run. It is very common that solar and clean energy supply part of the energy needs, as well as burning methane that comes off the wastewater. Wastewater treatment plants do use external power, but they don’t rely on it. The newest plants use renewable energy but have a connection to external power just as backup resource. When it comes to water utilities, it isn’t possible to have fully internal power resources. Desalination plants use lots of power that always require external power resources, as well as normal water suppliers that use pumps to move massive water volumes around, which doesn’t apply to wastewater. So supply chain attacks are a threat to Water utilities, but not as much of a threat to wastewater treatment plants.
Keeping Water Infrastructure Secured
The ever-evolving threat landscape requires a proactive approach to securing our water infrastructures. While the age of many facilities presents a challenge, it’s not insurmountable. Upgrading outdated systems with modern security protocols is certainly a step in the right direction, and implementing network segmentation can further secure critical operational technology (OT) networks from the internet and its threats.
About the author

Mariano Martín Tirado
Mariano is an advanced IT and OT expert with years of experience in Electrical engineering, communication networks, customised software and hardware solutions, and the application of new technology in the industrial sector. He is the technical leader responsible for the digitalization, technology and circular economy department at Acciona for water and wastewater treatment. He is passionate about using his expertise to drive innovation and to make a difference in the future of our planet. He holds degrees in both computer engineering from the college Innovation Luis Vives and in political science from the Complutense University of Madrid.
Share
Trending posts
How to Apply the NCSC/CISA 2026 Guidance
Webinar: 2026 OT Cyber Threat Report
2026 OT Cyber Threat Report
Stay up to date
Subscribe to our blog and receive insights straight to your inbox