Reframing the Wild Cyber GOOSE Chase with Sensible Segmentation
A cornerstone of our critical energy infrastructure is the electric power grid, a network of transmission lines and substations that crisscross the globe. Of the two, perhaps substations stand as the most complex and fragile element. Making substations more efficient is increasingly necessary, as an expanding grid requires an enhanced substation infrastructure based on digitization. However, resiliency has always been a necessity and should not be neglected in the name of efficiency. Ultimately, resiliency and efficiency are not possible to achieve without power grid cyber security. Many elements interface here, including SCADA systems, critical infrastructure, and suitability of the IEC 62443 standard. What’s most important, however, is how this all boils down to the IEC 61850 standards.
In a recent conference of the commanding standard available on the segment, IEC 61850 Week by Smart Grid Forums, the best and the brightest of the industry came together to evaluate the implementation of the standard and the novelties of its implementation. I personally love these conferences, full of excitement and with passionate engineers and practitioners, all rowing in the same direction. There was no shortage of questions after every talk. Virtualization at the substation was a big topic, but the spotlight was on the use and improvements of GOOSE (Generic Object Oriented Substation Event).

GOOSE is a communication model defined by the IEC 61850 standard, which uses fast and reliable mechanisms to group any format of data (status, values) and transmit it across communication networks within 4 milliseconds. This is most used to connect between substation IED (Intelligent Electronic Devices), which is great, as it allows not only efficient communication but also reliability and interoperability between vendors. To communicate between TSO (Transmit System Operators), IEC61850 also defines the MMS protocol, that uses a client server model, and can be routed over the internet.
At the conference, Waterfall Security participated in a panel alongside DNV and Rheebo. Rheebo opened the discussion with Intrusion Detection Systems and their role in substations. DNV provided useful information on the utilization of IEC 62351, the current standard for security in energy management systems and associated data exchange. Waterfall discussed the raise of attacks with physical consequences, and the role of unidirectional gateway technologies in a defense in depth architecture required by TSOs.
The topic of power grid cyber security appeared in many talks apart from the panel, mainly as part of methods to create encryption envelopes for GOOSE packets to route them as R-GOOSE, or as part of particular use cases such as remote access.
That’s All Good but… I Felt a Strange Déjà Vu From Three Years Ago
Back then I participated in a rail signaling systems conference, and all looked too familiar. Expert engineers discussing how to improve a real-time system, that was safety critical and used protocols that had no authentication nor encryption. While peppering their talks with some cyber security 101, they were noting that nothing could be done in the short term. In fact, due to the very work they were doing on standardizing the communication, this will allow an attacker to simply understand the protocol to create a destructive payload in a much shorter time frame.
Before I continue, let me bring up one important fact: Industroyer, the malware that left Ukraine without power for hours, and Industroyer2, the enhanced malware that recently attempted and narrowly failed this year, both include IEC 61850 destructive payloads.
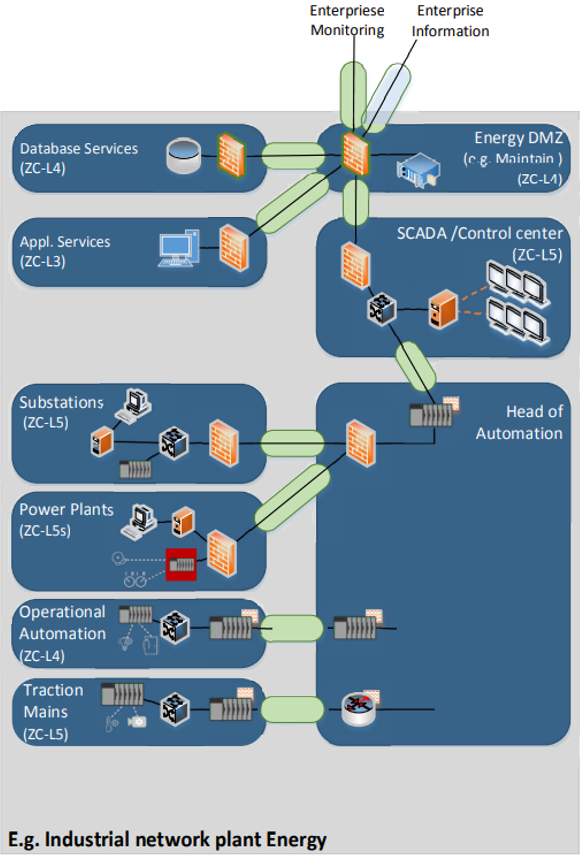
In the case of signaling systems, the industry acted, and TS-50701 was born. It requires strong segmentation for safety critical segments, including the substations, as they are essential parts of the rail network that electrify the train. Figure 1 is the example included in TS-50701 on how to segment rail power networks. In this example, the substation is in SL-5 (Safety) connecting to the Control Center, also SL-5 (Safety). Connecting safety networks to external networks requires Unidirectional Technologies or a very well managed – and probably expensive – DMZ .
But during the conference, segmentation was an afterthought and that was bothersome, given that we are talking about the power grid cyber security, a critical infrastructure . The problem here is GOOSE not only makes life simpler for the IED manufacturers, but also for an attacker to launch orchestrated attacks. R-GOOSE allows for the attacks to spread between substations. This is because, in most implementations, GOOSE is a multicast protocol with no authentication or encryption. And let me repeat, IEC 61850 has already been weaponized by nation state malware.
The “Aha!” Moment After the EE-ISAC Event at the European Parliament
Waterfall is a proud member of EE-ISAC (European Energy Information Sharing & Analysis Centre). The following week after I attended the Smart Grid Conference, I attended the EUTC and EE-ISAC event at the European Parliament, and the EE-ISAC plenary the next day.
During the event, MEP Pilar Del Castillo invited the European Commission, EE-ISAC, and the EUTC (European Utilities Telecom Council) to debate on what is needed to build resilient and cyber secure critical infrastructure in the Euro Zone. The most enlightening part of the event was of course over drinks. I was still rummaging about what happened at the event the previous week when I started a chat with Stephan Lechner, Director of Euratoms Safewards (DG ENER.E). He discussed an article he authored (link below) on reviewing the cyber security strategies for the European grid. In that review, three elements stood out:
- The real-time performance requirements of the power grid do not allow for overhead, so standard cyber security elements such as authentication are not readily available.
- the impact of successful attacks may create a cascading failure effect.
- Existing, legacy systems need to interact with new devices, increasing the risk of cyber attack
All of this applies directly to what I learnt the previous week! GOOSE is a real-time protocol, that in most implementations lacks security. R-GOOSE allows for interconnecting substations, thus increasing the risk of cascading effects. Techniques, such as virtualizing substation IEDs, merges legacy systems with very capable datacenters, which are much more susceptible to attacks as they use commercial off-the-shelf software. However, the architecture and segmentation TSOs operate today lag behind similar critical infrastructure in the EU. Industries here, such as rails, have adapted IEC 62443 with great care to fit the requirements in TS-50701. Quoting directly from the article:
“Operators of transmission and distribution networks must be aware of the specificities of their technologies and networks and should not copy cyber security concepts from other industry sectors without adapting them carefully.”
Bingo!
Final Thoughts
Waterfall Security Solutions and I will be at ENLIT, co-hosting a booth with EE-ISAC. There, I will have the chance to chat with the experts I met at both conferences. It’s clear: Substation security needs to be redefined to fit the increasingly high stakes of improving the resiliency of the EU power grid. The hard work of IEC 61850 to ensure the interoperability of elements in substations, and the realization of true digital substations, needs to be backed up with strong strides to sensitive security measures that consider the realities of transmission and TSOs. Segmentation according to strict standard should be a starting point, following the steps of similar critical systems with similar issues, such as rail signaling systems.
References and Further Reading
European Cyber security Journal, Volume 6, Issue 1, Page 22
ENLIT Europe – Waterfall partner profile
EUTC and EE-ISAC event at the European Parliament
