Edge network monitoring looks at the lowest level and arguably most important industrial networks, not the networks closest to IT, which are the more typical focus of industrial network monitoring and intrusion detection. Ron Fabella, CTO and Co-Founder of Synsaber joins us to look at the problem the other way around – at how important and how useful it is to monitor our lowest level networks – the “edge” networks closest to the physical process.
Listen now or Download for later
THE INDUSTRIAL SECURITY PODCAST HOSTED BY ANDREW GINTER AND NATE NELSON AVAILABLE EVERYWHERE YOU LISTEN TO PODCASTS

Such monitoring can be very valuable but can also have significant challenges. Edge networks in pipeline pumping stations and power grid substations can be hundreds of kilometers from corporate or SCADA system central offices, with only costly and low-bandwidth communications available back to those central locations. Edge networks can be much more numerous than central networks – a large transmission operator might have over a thousand high-voltage substations for example. If we want to monitor all of the device-to-device traffic in these substations, we almost certainly need a device in each substation to do the monitoring, analysis and summarize results to a central SIEM or Security Operations Center (SOC).

Changing Industrial Communications
At the same time, industrial communications patterns are changing. There was a day when PLCs and other devices communicated with the central SCADA / DCS computers and nothing else. To monitor all of your “edge” devices, it was almost enough to monitor only the central SCADA networks, because the remote devices talked to only the central systems.
In today’s automation, we increasingly see devices close to the physical process talking to each other. In the new IEC 61850 protocol, for example, we see devices in substations broadcasting information to each other across Ethernet hardware. In fact, we may see protective relays in those substations communicating with relays in adjacent substations when line faults occur, to figure out how far down the line the fault lies, and to protect expensive equipment in adjacent substations.
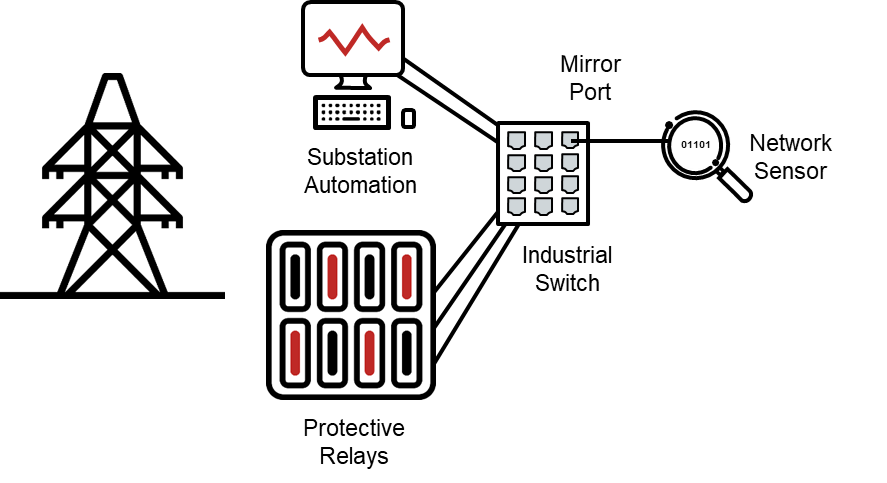
Demystifying Edge Network Monitoring
Historically, a lot of people regarded industrial communications protocols as very hard to understand. Monitoring networks closer to IT networks was seen as “doable” for an IT security team, because the communications protocols (TLS, HTTPS, DCOM, SMB) that were used on those high-level industrial networks were the same as protocols used on IT networks, and therefore familiar to IT security analysts.
An important point Ron makes is that the “opaqueness” of industrial protocols has been over-hyped. Protocols are protocols. A lot of them are standard. Even the proprietary ones are just protocols. If the OT intrusion detection system understands the protocols, it can alert SOC analysts using terminology that makes sense to those analysts. “Someone just updated the firmware in the device.” “Someone just wrote to a part of the device that we’ve never seen anyone write to before.” Make sense of these alerts and correlating these alerts with change orders and work orders that may be open for the devices, or not, is very much doable for security analysts with a reasonable depth of understanding of communications protocols generally and industrial devices and their functions specifically.
Edge Network Monitoring is Upon Us
The bottom line of the episode? Today, monitoring industrial operations at the edge is not only valuable, but practical. Listen in for the details.




