The Hospital Clinic in Barcelona recently suffered a ransomware cyberattack. This ransomware affected the services of the 819-bed hospital, postponing hundreds of surgeries and canceling thousands of visits.
Coincidentally, this is the hospital where my daughter was born.
But today I am going to discuss the threat actor, and the evolution of ransomware. The alleged ransomware gang behind many of these attacks routinely declares themselves to be “the good guys.” No, they are not the good guys. But let’s play devil’s advocate here. If they are the good guys, who are the “bad” guys? And let’s go further; who could be the “ugly” guys of the ransomware world?
The “Good Guys”
The “good guys“ in the world of ransomware are those who stick to their end of the bargain. They encrypt your data and offer to return your own data to you in exchange for payment. If you refuse to pay, they leave your data encrypted and move on. In the case of Ransomhouse, they usually just focus on threating exfiltration of the capture data.
Ransomhouse, the group identified by the clinic as the perpetrator, represents a strange evolution in ransomware groups. They have a Telegram group, and their webpage reads like a hacktivist group. However, most of the public, including many Telegram users, do not agree with this view, particularly as hospitals are a common target for the group.
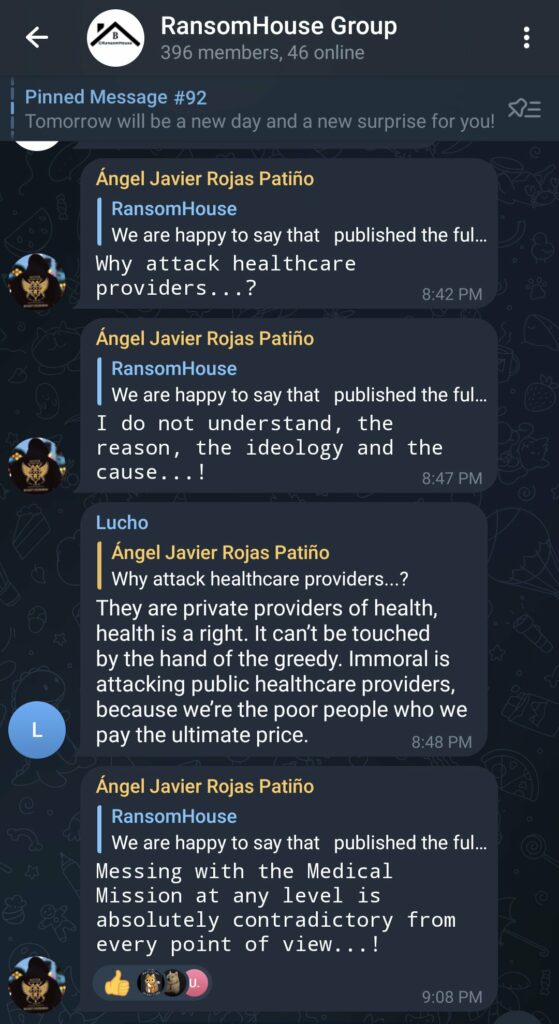
The group’s manifesto, as outlandish as it seems, claims that they are improving cybersecurity at the affected sites. The manifesto states that they are doing this for the good of society, because the consequences of what may come next could be worse. In essence, they hold the corporations responsible for inadequately safeguarding their networks and for offering “absurdly low” financial incentives for disclosing security vulnerabilities.
They have a point: cybersecurity in hospitals, particularly regarding the protection of physical operations, is not where it should be, and the consequences could escalate. When I visit a hospital, I tend to examine the computer systems – a habit from my previous life as a penetration tester. Often, during consultations, the doctor leaves the room, leaving USB ports and even the screen unlocked. I have been able to infer the login credentials of many practitioners. This is not the doctors’ fault; they want to help their patients, but it’s evident that many hospitals lack even the most basic cybersecurity training.
Of course, this is just my personal experience, but the consensus is that the cybersecurity of hospitals leaves a lot to be desired. More importantly, the critical devices used to perform surgeries, operations, screenings, and other essential tasks are often insecure by default, as demonstrated by initiatives such as the Hippocratic oath for medical devices.
As a result, hospitals are becoming increasingly attractive targets for cyber criminals due to their vulnerability. However, things are changing: hospitals now often decide not to pay.
So who are the “Bad Guys”?
In the past, ransomware demands were routinely paid. Today, that is not the case, with 61% of hospitals paying (still more than the global average of 46%), and this number is steadily decreasing.
So “bad guys” are appearing, that do not stop in encrypting the data, and try to add more pain to force the victims to pay out. And indeed, due to the lack of payment, ransomware attacks are becoming more vicious, or as Wired puts it, entering a “heinous” new phase. For example, the Russia-linked Blackhat ransomware group posted sensitive clinical photos of breast cancer patients, labeling them as “nude photos,” to extort money from the Lehigh Valley Health Network (LVHN).
Will they stop there? Is there anything else the actor can do that may cross a line?
Enter the “Ugly”
Without forgetting the severe consequences for patients’ privacy, lets focus for a second on the physical consequences of these attacks, which typically last for a week, including cancellation of surgeries and appointments.
As damaging as ransomware is when affecting services, the truth is that today’ attacks are not intended to create physical consequences. These consequences are a byproduct of the unavailability of patient data, and the fact that certain software may have been rendered unusable. The attacks are meant to extort money by denying access to data, or by menacing with exfiltrating and exposing private data.
The goal is not to stop the HVAC systems required to keep patients cool, disable the lights, or shut down the elevators needed to move patients from floor to floor. In the attack to Hospital Clinic the ransomware led to the cancellation of more than 300 surgeries, but no equipment was damaged, no emergency surgery needed to be interrupted and no one died – at least, we hope – as a direct result of the cyberattack. But we know the devices used for surgeries are consistently insecure and easy to hack. We have been discussing in our blogs how we are in a new age of OT: the age of physical disruptions. These disruptions impact the daily lives of everyone, but purposely disrupting equipment during surgeries, or medical dosing equipment, or other equipment in intensive care units?
Calling the Real Good Guys
Hospitals and healthcare providers are critical infrastructure, and new regulations such as NIS2 categorize them as such. It is essential to recognize their importance as they form an integral part of our well-being. An attack aimed solely at causing damage to a hospital could have catastrophic consequences. There is a real risk that ransomware gangs will become increasingly sinister by demanding money in exchange for not damaging equipment or, even worse, putting patients’ lives at risk.
Today, hospitals have inconsistent protection. Board members in private hospitals and government officials in public institutions must understand that enhancing healthcare involves not only exceptional professionals and facilities but also robust defenses against these kinds of threats. Hospitals cannot depend on the “good will” of cyber attackers. Current attacks have exposed a problem: attackers claim they could do more harm – and unfortunately, they are right – so they call themselves the good guys.
Let’s not wait for the ugly ransomware actors to emerge before taking appropriate action.
