In the ISO 27001 (2022) introduction section 0.1, the standard states that it provides requirements for a security management system, and that such a management system:
“preserves the confidentiality, integrity and availability of information.”
The standard is all about protecting information. This is a source of great confusion in many industrial enterprises however, because as NIST 800-82 points out, the top priorities for physical industrial operations is almost always to protect safe and reliable operation of the physical process from cyber threats, not to protect information.
Now, information security “purists” argue that in modern industrial control systems, it is network messages that communicate monitoring and control information to the computers controlling the physical process, and so protecting that information is essentially the same as ensuring correct, safe and reliable control. On the surface this rings true, sort of.

The problem is that, in my experience, trying to explain this to engineering teams is like standing on your head and saying “You know, if you look at the world this way, it all makes sense! It’s all information! Protect the information!”
Engineering teams care much more about physical safety – not being killed in a fire or explosion at work and never seeing their kids again – than they care about information. And they care enormously about reliability as well – ensuring that the multi-billion dollar investment in the physical infrastructure that is a power plant or refinery or rail system continues operating. Physical operations are the focus at industrial sites, not information.
Control vs. Monitoring
But the confusion is worse than that. When we insist that cybersecurity at industrial sites is all about protecting different kinds of information, we blind ourselves to the deep differences in risk that are characteristic of different kinds of data. I mean – imagine that we are a technician checking on the status of a 6-story catalytic cracker at a refinery – a device full of very hot, pressurized hydrocarbons. We are standing there running through our checklist on our tablet computer when we notice that outside the fence around the refinery, someone has set up a telescope looking at the cracker. We walk around to that side of the cracker and we see a gauge. That person appears to be stealing the temperature reading from the gauge. What do we do? Maybe nothing. Maybe we call security and report the theft, because the temperature setting may be a trade secret after all.
Now imagine a different scenario. We are that same technician, in front of the same cracker, working through our status check checklist, when a stranger runs up to this massive device through a hole in that same fence. He runs up to the temperature set-point dial on the side of the cracker and cranks the dial hard right – increasing the set-point to a dangerously high value. What do we do? We scream for security. We run up to the gauge and shoulder the intruder aside, still screaming, turning the gauge back to its proper setting. Or maybe we run the other way, still screaming for security, heading for the big red safety shutdown button to trip the plant before disaster strikes us.
What’s the difference? Monitoring data is data that leaves the facility. The consequences of tampering with or stealing data that leaves the facility is similar to the consequences of tampering with or stealing any other data in the ISO 27001 protected IT network. Control data however, is data that enters the facility from outside – in the head of the intruder in our example above. Tampering with control data is enormously more dangerous than tampering with monitoring data.
Saying “it’s all information, protect the information,” as ISO 27001 says, ignores this deep difference between monitoring data leaving the plant, and control data entering the plant. Or for that matter, monitoring data leaving the OT network for the IT network, and control data entering the control network from the IT network. Instead of a focus on “protecting the information,” what we really need in many industrial operations is to figure out how we can protect safe and reliable physical operations FROM information – more specifically from malicious control information entering our control networks.
ISO 27001 and Security Engineering
The emerging discipline of security engineering is very much focused on protecting physical operations. The goal of security engineering is not to protect the data, but to use engineering techniques to prevent unacceptable physical consequences due to cyber threats. The engineering profession after all, has been managing physical threats to public safety for most of a century. What confuses people familiar with ISO 27001 is that the tools and techniques available to the engineering profession often look nothing at all like the tools and techniques routinely used in 27001 programs – for example:
- over-pressure valves eliminate the risk of boiler explosions due to cyber manipulation of furnaces,
- manual operations fall-backs ensure that critical infrastructure can continue to be operated, even if control system computers have been crippled, and
- unidirectional gateways enable monitoring data to leave industrial networks without permitting any potentially malicious control data back into industrial networks.
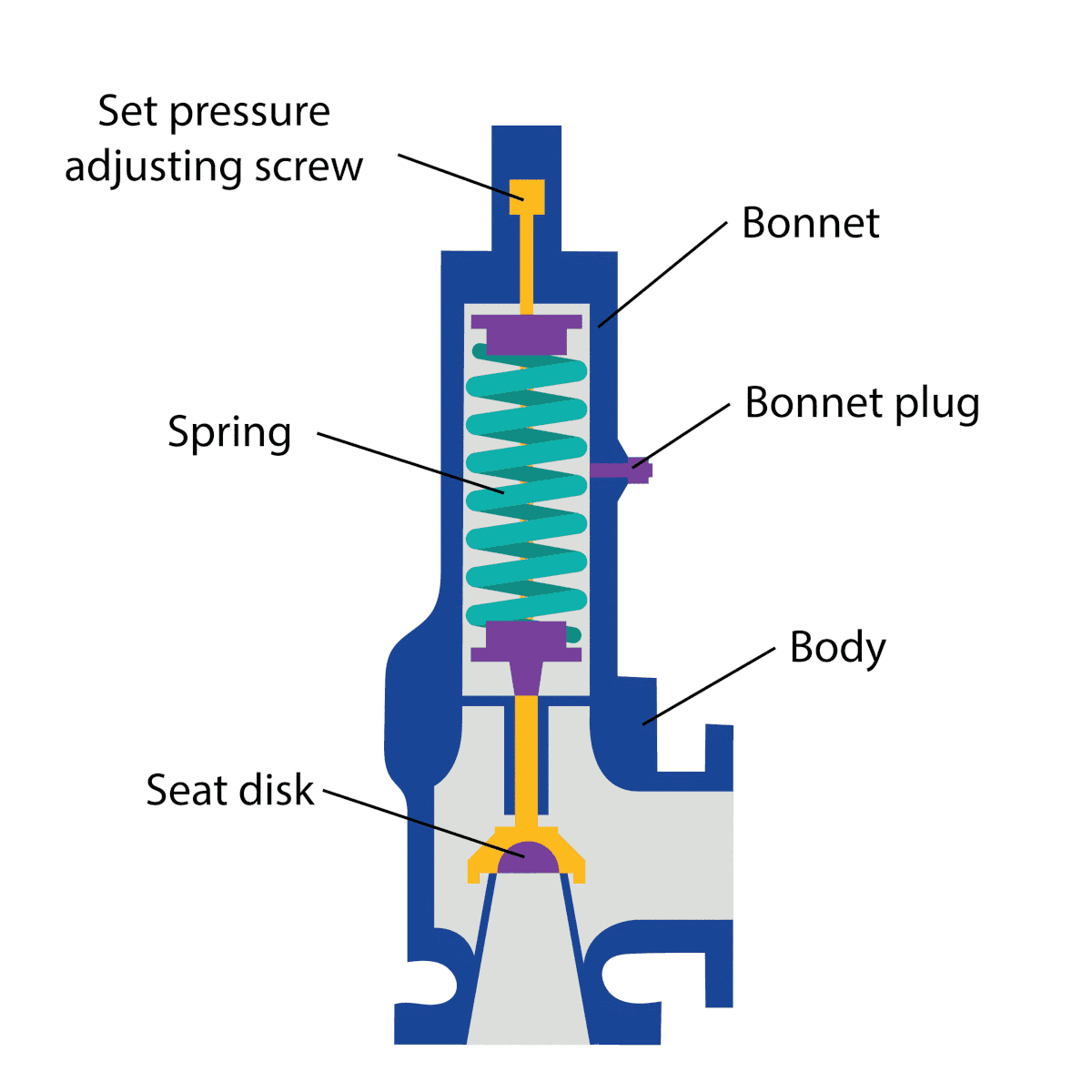
Where are the over-pressure valves mentioned in the ISO 27001 standard? The valves are not there. Over-pressure valves are not cyber security mitigations. They are physical mitigations for a variety of threats to safety, including cyber threats. Increasingly, people are calling this class of solution “engineering-grade” solutions. Engineering-grade solutions are deterministic – they do the same thing, all the time, no matter what happens in the threat / risk environment.
ISO 27001 Gets Even More Complicated after Certification
When an organization achieves ISO 27001 certification, it is generally the entire organization that is certified – including all of the industrial sites and other physical operations, if any. This in spite of the fact that “protecting the information” is a very poor fit for managing physical risks due to cyber assaults. In spite of the poor fit, if we must comply with corporate-wide ISO 27001 imperatives, we are going to need to use the 27001 language and approach, at least some of the time.
Worse, some physical operations really do have important confidential data and trade secrets that they must protect – consider for example pharmaceutical manufacturing, or automobile manufacturing. In this case, we really do need to protect the (monitoring) data, in addition to preventing malicious control from sabotaging operations.
Bottom Line on 27001
The bottom line is that we should not be applying ISO 27001 definitions and techniques blindly in industrial settings. Much of the time those definitions lead us astray, and blind us to engineering approaches to managing physical risk due to cyber causes. To succeed, we must:
- Bring engineers and enterprise security people to the table – so that security people can explain what must be done to satisfy ISO 27001 certification requirements, while engineers explain what they can do to take the most damaging physical consequences of cyber attacks entirely off the table,
- Understand our data flows, and the potential consequences of compromising / stealing monitoring data on the way out of the industrial site, and
- Apply engineering-grade solutions to the task of controlling or even eliminating entirely the possibility of compromised control information entering our control-critical networks.
Yes, in today’s increasingly ISO 27001 certified enterprises, industrial users have to talk enough “protect the information” talk to keep the 27001 audit team happy. But we must not confuse monitoring information with control information, nor confuse cybersecurity mitigations with engineering-grade designs that eliminate large classes of risk entirely, and have done so reliably, sometimes for generations.
