Cyber Security for Rail Industry
Rail Industry Cybersecurity – Cyberattacks on rail systems can result in service outages or much worse: derailments, toxic spills, equipment damage and even mass casualty events. The rail industry has been focused on safety for over a century, and in the modern world, cybersecurity is essential to safety.
Waterfall’s Unidirectional technology is used to secure industrial controls for railways such as the signaling system, as well as rail operation control centers.
Operations Control Centers
Cybersecurity programs must assure safe and continuous operation, while enabling essential data flows and remote access needed for efficient system and business operations.

Signalling Systems
Engineering-grade cybersecurity programs must deterministically and extremely reliably prevent tampering with any aspect of signaling systems, while enabling network visibility and security remote access into these very critical systems.
Metro Stations
Cyberattacks that impair escalators or lighting in metro stations deep underground pose a public safety risk and can severely impact operations at peak periods. Unidirectional solutions that enable real-time monitoring and secure remote access for new or developing problem conditions, without introducing the cyberattack paths that always accompany IT/OT firewalls.

With Waterfall you get

Safe IT/OT Integration
Unidirectional Gateways provide rail system business automation with access to OT / industrial data such as equipment usage for predictive maintenance and automatic spare parts ordering, without providing attackers or malware access to the industrial systems that are the sources of that data.

Secure Remote Access
Waterfall’s HERA® , Hardware-Enforced Remote Access, provides the functionality of remote access, without the inherent risks and threats that come with network connectivity.

Worker and Passenger Safety
Unidirectional Gateways help to assure the safety of passenger rail systems as well as the safety of workers who are maintaining tracks and systems.
Use cases
Signalling system monitoring
Waterfall for IDS provides unbreachable, engineering-grade protection for signalling systems and other vital systems, while enabling industrial intrusion detection systems to be deployed safely and integrated with enterprise-based and even cloud-based Security Operations Centers.
Passenger Notifications
Unidirectional Gateways safely replicate SQL Server and other databases of locomotive locations out to enterprise networks and cloud servers, so that passenger cell phone apps know when trains will arrive at which platforms, with no risk from compromised cell phones or other Internet-based threats.
Remote Access
Hardware Enforced Remote Access (HERA® ) enables remote management, updates, and troubleshooting for OT networks, safely. When software-based secure remote access is too great a risk, HERA® ‘s hardware provides remote functionality without the risks of remote connectivity.
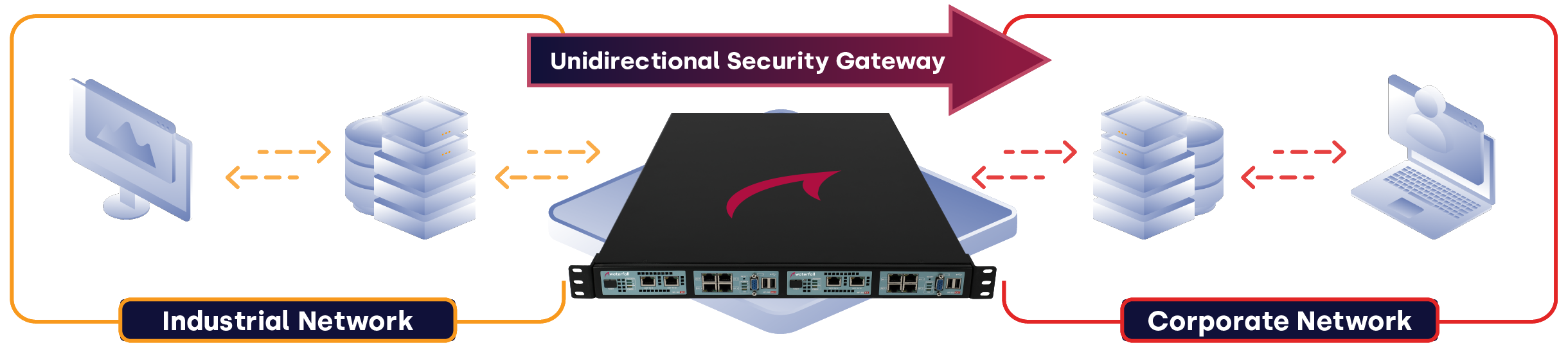
How it works

Connect
An industrial network safely to an IT network

Protect
The industrial network with hardware enforced technology

Replicate
Real-time operational servers to the enterprise IT network