Stakeholder-specific vulnerability categorization (SSVC) is a new alternative to the common vulnerability scoring system (CVSS) used in the Common Vulnerabilities and Exposures (CVE) database. In this episode, Thomas Schmidt of the German BSI (Federal Bureau for Information Security) joins us to look at the new system, how it works, and where to use it. In the end, SSVC looks to be a new kind of tool, like CSAF and Malcolm that the BSI and others are promoting to help critical infrastructure and other industrial organizations enhance their cybersecurity.
Listen now or Download for later
THE INDUSTRIAL SECURITY PODCAST HOSTED BY ANDREW GINTER AND NATE NELSON AVAILABLE EVERYWHERE YOU LISTEN TO PODCASTS
The episode starts by comparing the new SSVC with the older and more widely-used CVSS:
- CVSS assigns a score to a vulnerability between 0 and 10, with 10 being the most severe kind of vulnerability. CVSS assigns a score based on the characteristics of the vulnerability.
- SSVC helps individual businesses or sites decide on what action to take on a specific vulnerability, based both on characteristics of the vulnerability and information as to how the vulnerability might affect the business or site.

SSVC Actions and Criteria
Thomas explains that with SSVC, actions that a site might take if a vulnerability applies to software deployed at the site can include:
- Track – take no action right now, but keep watching the vulnerability,
- Attend – alert decision-makers in the organization to the vulnerability and look hard at doing something about the vulnerability (patching or compensating measures) sooner than “normal”.
- Act – the vulnerability requires immediate attention, analysis and probably remediation.
Unlike CVSS that looks primarily at a vulnerability, the kind of software a vulnerability is found in, how exposed to attack that software tends to be etc., when prioritizing a vulnerability, SSVC looks at specifics of the vulnerability within the context of a specific organization. This means that the SSVC rating for a vulnerability is generally not re-usable across organizations or sites – it tends to be unique to an organization. SSVC looks at criteria including:
- Exploitation – is there a public POC or evidence that the vulnerability is being exploited in the wild (this criterion can change value over the lifetime of the vulnerability)?
- Technical Impact – does the vulnerability give the attacker total control over the target software, or something less than that?
- Automatable – are steps 1-4 of the kill chain (reconnaissance, weaponization, delivery and exploitation) automatable?
- Mission Impact – if the vulnerable software at your site is compromised, what is the impact on your mission? Eg: in a rail system, is the entire system shut down, or just one section of track? In a refinery, is the entire site shut down, or only one production unit?
- Public Impact – if you are serving the public, how serious is the impact on the public (eg: minimal / material / irreversible)
SSVC also tracks mitigation status – how difficult it is to do anything about the vulnerability, but this is only for information purposes. How difficult it is to do anything does not determine how serious the vulnerability is for a site, or how urgently the site needs to take action, or not.
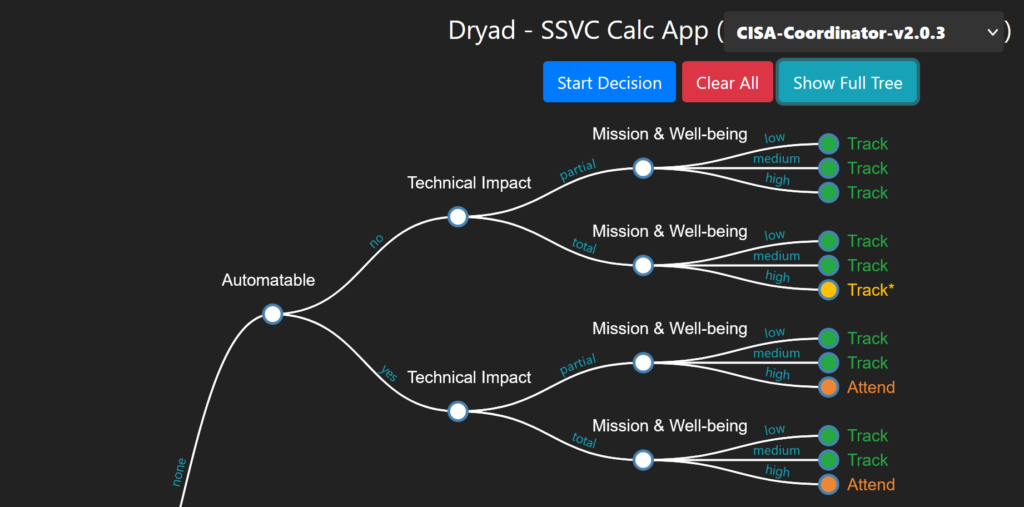
Using SSVC
All of these factors are connected into a decision tree. An example calculator that can help you walk through the decision tree is available at:
The calculator asks questions about the vulnerability’s exploitability, technical impact, public impact and so on above and results in a recommendation of what to do about the vulnerability: track, attend or act.
On the surface, this looks like a lot of work. There are thousands of vulnerabilities announced every year. CVSS priorities for the vulnerabilities are published in the CVE and other vulnerability databases, but SSVC action recommendations cannot be published – every recommendation is unique to a business or site. Every business or site has to go through the SSVC decision process themselves for every vulnerability to decide what to do about the vulnerability.
In a sense, however, this is no surprise. Most sites have to do this anyways to one degree or another – they cannot use the CVSS ranking exclusively to decide what to patch, because circumstances of each site and each vulnerability differ. This is what SSVC recognizes. SSVC in standardizes the decision process – in part hoping that various vendors will be able to produce asset inventory and other tools that take in information about a specific business or site, and can then use that information as well as CVE and CVSS information to produce an automatic recommendation for each site about what that site should do for each of the tens of thousands of vulnerabilities the site has to look at every year.
So tune in for the conversation with Thomas Schmidt and learn more about the SSVC system.



