Selecting OT “Secure” Remote Access Solutions – Options, Criteria & Examples
Which OT remote access solution is right for you?
Andrew Ginter

Which OT remote access solution is right for you? It depends on the sensitivity of your OT/physical process, on your risk tolerance, and on your assessment of credible threats. In Waterfall’s upcoming webinar, we look at the landscape of available OT remote access solutions, how they compare risk-wise, and what a decision tree for choosing between the alternatives looks like.
One core assumption: we are trying to prevent cyber attacks pivoting from the Internet (possibly via intervening IT and other networks) into sensitive OT networks and sabotaging physical operations
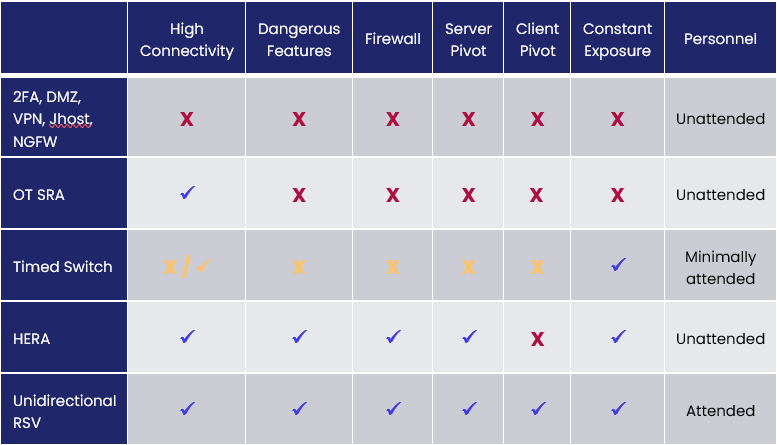
In our webinar on April 21st, we look at different types of systems:
- 2FA, DMZ, VPN, Jhost, NGFW – this is a conventional IT/OT remote access system, such as the system described as the minimum acceptable for NERC CIP Medium Impact sites, including (more or less) two-factor authentication, a demilitarized zone “network between networks,” a virtual private network, a jump host, and a next-gen firewall.
- OT SRA – is a typical OT “secure” remote access solution that works roughly like Microsoft Teams – there is a client in the OT network and it reaches out through an IT/OT firewall to connect to remote laptops and other clients, either by contacting those clients directly or by reaching into a cloud service or other server to rendezvous with clients.
- Timed switch – a timed hardware switch that temporarily connects / disconnects a conventional type (1) or (2) software-based remote access solution to an IT network or the Internet. The timed switch is normally in a disconnected state and enables temporary remote connectivity infrequently.
- Hardware-Enforced Remote Access – Waterfall’s HERA, which consists of cooperating inbound and outbound gateways designed to prevent attacks pivoting from the Internet into OT systems.
- Unidirectional remote screen view technology – tech that lets the remote user “look but not touch” and requires an engineer or other human operator in the protected OT network to cooperate with the remote expert providing remote support.
Features & Characteristics of Remote Access Solutions
To compare risks in these solutions, we look at a number of features & characteristics:
- High connectivity – CISA and other authorities recently requested that high-consequence sites stop using VPNs for remote access, in large part because VPNs very often provide more connectivity into IT and OT networks than is needed and is wise.
- Dangerous features – many “secure” remote access solutions have a myriad of features including dangerous ones such as file transfers (of potentially malicious files) and clipboard cut-and-paste operations (of potentially large attack scripts).
- Firewalled – most “secure” remote access solutions demand a firewall at the IT/OT interface. Firewalls have a role inside OT networks and inside IT networks but are often not strong enough to defend a consequence boundary – when OT and IT networks have dramatically different worst-case consequences of compromise.
- Server pivot – most “secure” remote access solutions have fairly constant IP addresses. They are in a sense “sitting ducks” for any adversary who cares to test them, any time that adversary cares to test them – for zero days, for unpatched known vulnerabilities, for misconfigurations and so on. And once these remote access servers are compromised, the attacker can pivot through the compromised remote access equipment, using the compromised equipment to attack more valuable assets deeper into the OT network.
- Client pivot – most remote access solutions can be mis-used by attackers if he remote workstation or laptop is taken over. Two-factor authentication makes this harder, but not impossible, since 2FA is also software with vulnerabilities, both known and zero-day. Attackers thus are able to pivot through a compromised remote endpoint into the protected OT network.
- Constant exposure – most remote access solutions are “always on” – constantly exposed to attacks from compromised external networks, such as IT networks and the Internet.
- Personnel – most remote access solutions are designed for unattended operation, meaning that no OT personnel need be present at or internally connected to remote sites, such as substations, pump stations, lift stations, compressor stations or other remote installations. Attended operation systems that work only if there are local personnel present to help them along tend to be more secure, but those personnel are not always available.
How do we use these characteristics to choose between the options?
Well, we need to understand our needs and especially the criticality of our physical operations. A key question: what is the worst consequence possible due to a credible attack scenario? The question has three key parts:
- Worst possible consequence – what is the worst that can happen if compromised computers either fail to function correctly, or more often are deliberately made to function maliciously. And beware – many risk programs have blind spots, such as bricked control equipment. What happens if the bad guys get in and load dummy firmware into most of our 10-year-old PLCs, damaging them so thoroughly that it is now impossible to reload them with correct firmware? Where do we get spares to replace these components when the manufacturer no longer produces this equipment?
- Credible attacks – in the spectrum of possible attacks (see Waterfall’s report on the Top 20 Cyber Attacks on Industrial Control Systems), which attack scenarios and consequences do we deem credible threats, given the defenses we have already deployed and the remote access systems we are considering, and which consequences and attacks do we not believe will be realized in our network or in any similar networks, any time soon?
- Acceptable consequences – which credible consequences, due to credible attacks on our systems, do we deem acceptable vs. unacceptable?
All this and more, in greater detail, with industry-specific examples, is coming up in our Apr 21 webinar ‘Building a Game Plan for OT Remote Access‘.
I hope you can join us.
About the author
Andrew Ginter
FAQs About Remote Access Solutions
What are the different types of remote access solution?
2FA, DMZ, VPN, Jhost, NGFW – this is a conventional IT/OT remote access system, such as the system described as the minimum acceptable for NERC CIP Medium Impact sites.
Another type is OT SRA, which is a typical OT “secure” remote access solution that works roughly like Microsoft Teams.
Timed switch – a timed hardware switch that temporarily connects / disconnects a conventional type (1) or (2) software-based remote access solution to an IT network or the Internet.
Hardware-Enforced Remote Access, like Waterfall’s HERA, which consists of cooperating inbound and outbound gateways designed to prevent attacks pivoting from the Internet into OT systems.
And finally, unidirectional remote screen view technology which lets the remote user “look but not touch” and requires an engineer or other human operator in the protected OT network to cooperate with the remote expert providing remote support.
What are the main features and characteristics of a remote access solution?
The main features and characteristics of a remote access solution are the degree of connectivity, the location of firewalls, server & client pivots, exposure time to potential attacks, and the personnel required to operate them.
How to choose between different remote access solutions?
To know which remote access solution to choose, we first need to understand our needs and especially the criticality of our physical operations. A key question to answer is: what is the worst consequence possible due to a credible attack scenario? Once we understand what is at stake, we will have a better understanding of how to choose the solution that prevents this scenario from occuring.
Share
Trending posts
IT/OT Cyber Theory: Espionage vs. Sabotage
Ships Re-Routed, Ships Run Aground
Stay up to date
Subscribe to our blog and receive insights straight to your inbox