This is the second blog in the series, following Segmentation 201: Unidirectional Gateways vs. Firewalls. Unidirectional architectures are network segmentation solutions that feature at least one Unidirectional Gateway. These architectures may also incorporate other elements such as an additional Unidirectional Gateway, a reversible feature in the unidirectional gateway, or a temporary bypass. A key to unidirectional architectures, in addition to the protection offered by the unidirectional hardware, lies in the software element, which replicates data and data sources unidirectionally.
Despite their growing significance in protecting industrial automation systems, unidirectional architectures are often not well understood, particularly by professionals with IT-centric backgrounds. Unidirectional architectures represent a true revolution in OT network cybersecurity.
Today, we not only have one-way perimeter solutions, but we also have one-way architectures – the adoption of which is undoubtedly increasing. This is especially true with the introduction of strict physical segmentation requirements in pipelines and rail systems, the rise of ransomware attacks, and the emergence of the industrial cloud. I see opportunities for this class of architecture even in many IT-centric verticals, such as banks and financial institutions.
In this article, I will strive to provide a clear explanation of unidirectional architectures and why they are becoming increasingly important in industrial systems.
Traffic flow in OT networks
Before diving into the specifics of unidirectional architectures, we must first understand the basic principles of data flows in industrial systems. In these systems, data is generated and collected by various devices and sensors. It is then processed, analyzed, and potentially sent back to control the industrial processes, modifying interactions with the physical world.
Note: Unidirectional Gateways are generally not deployed within the industrial network – bi-directional traffic between control system HMIs and PLCs are not amenable to this class of protection. The gateways are deployed almost exclusively at connections between industrial networks and external networks such as enterprise networks or the Internet.
As discussed in my previous articles, most OT networks, when connecting with enterprise IT networks, exhibit asymmetric traffic: A significant amount of data is sent outbound for use in the enterprise network or beyond, and some data may be sent back into the industrial network from external sources. In most cases, we can exploit these asymmetric data flows to our advantage, replacing one or more firewalls with unidirectional architectures. Going forward, when I refer to outbound traffic, I am referring to traffic flowing from an OT network, whose worst-case consequences of compromise are unacceptable physical consequences, to an IT network, whose worst-case consequences are lawsuits or other business losses for which we can more easily buy insurance. Inbound traffic refers to data sent in the reverse direction.
In IT architectures, where there is no such clear division, the primary objective is to transfer and process data. Due to this, network segmentation in IT networks historically focuses on preventing applications and specific network addresses from traversing between networks using firewalls. Firewalls have evolved over the years, but the core concept remains the same – filtering packets using software.
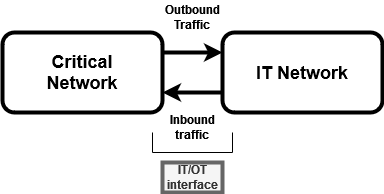
Inbound and Outbound traffic: Role in security
Inbound data sent to OT networks is responsible for directing and controlling the behavior of various elements in the system. This includes tasks such as firmware updates, communicating new production orders and quality requirements to the production system, and so on. Outbound data, on the other hand, typically consists of quality readings, raw materials and finished goods inventory levels, equipment usage readings and other information sent from the various sensors and devices in the system, as well as from databases and historians. This data is used to monitor the status of the system, detect and diagnose problems, and so on.
The security objectives for these two traffic patterns differ, particularly regarding the criticality of inbound information. Compromising the integrity of outbound data, for example, such as altering quality readings, has business consequences, such as delaying and resampling of a batch of product that is reported as sub-standard. Such compromise generally impacts the business less than tampering with inbound data, such as data determining what the quality requirements for the product are, which might lead to a large batch of unsaleable product actually being produced.
To enhance security and reduce the opportunity for cyber attacks causing serious consequences, our objective should be to decouple inbound and outbound data flows. Unidirectional technologies very naturally and unavoidably separate inbound and outbound traffic. This task is typically performed at the IT-OT interface but could be implemented in other locations within the network.
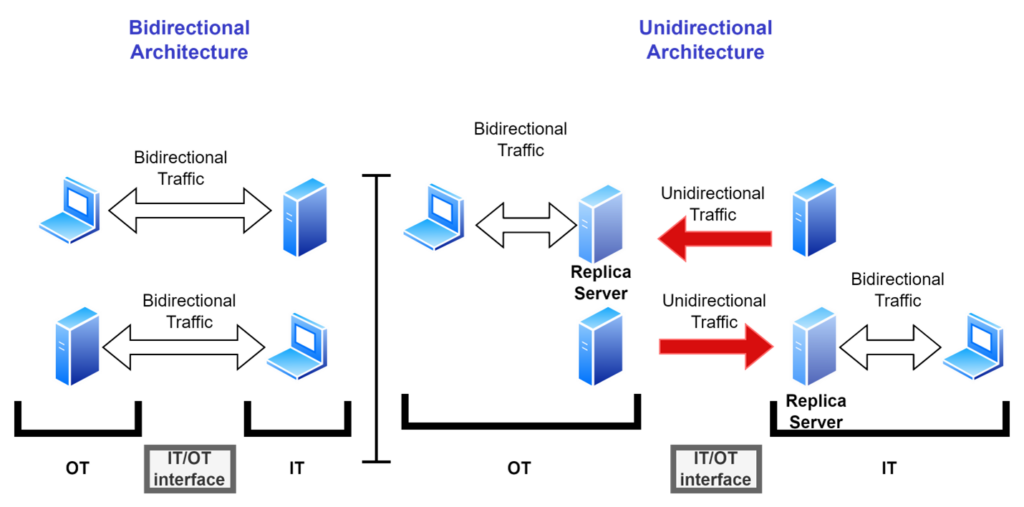
However, this separation can be challenging, since current applications often use the same protocol and applications to both transmit and receive information on the same connection. This is due to OT networks employing IT products and protocols. For instance, the TCP/IP protocol is the workhorse of modern networking and almost all application layer protocols that use TCP/IP are query/response. Clients send queries into servers that are data sources requesting specific data, and the servers reply on the same connection. This creates a potential attack vector, as the queries could be altered in an attack to manipulate the industrial server, and through the server the rest of the industrial control system. By re-engineering the networks and utilizing replication, this issue can be resolved in almost all cases. Let’s examine the following figure:
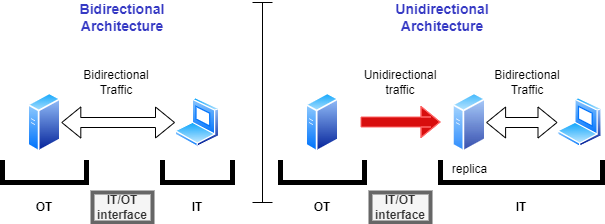
In the figure, the Unidirectional Gateway is a client of an industrial data source, such as a historian server. The gateway sends queries to the server asking for all new or changed data. On the enterprise network, the gateway logs into the enterprise historian server and inserts the data into that server. Any enterprise users or software applications that need the industrial data can now query the enterprise historian. All of the data that is permitted to be shared with the enterprise is available in the enterprise historian. No queries need be sent back into the industrial network through the gateway any more.
Unidirectional architectures are widely understood as “permitting information to flow in only one direction.” However, this example is just one use case – the most common use case – where we completely cancel inbound traffic. In the following sections, we will explore this and other architectures currently in use.
Unidirectional Architectures
There are five unidirectional architectures in widespread use today:
Pure Unidirectional: Information is replicated in one direction only. Only outbound traffic is allowed, and inbound traffic is physically blocked. This is what most people think of when they hear “unidirectional gateway,” and it is a common implementation for many OT use cases.
Typical use cases include monitoring production levels and equipment usage in refining and power generation. Unidirectional gateways for these use cases are often deployed at the OT-IT interface, where it is easier to differentiate between inbound and outbound traffic. These use cases may include unidirectional Remote Screen View connections, that enable remote support for vendors.
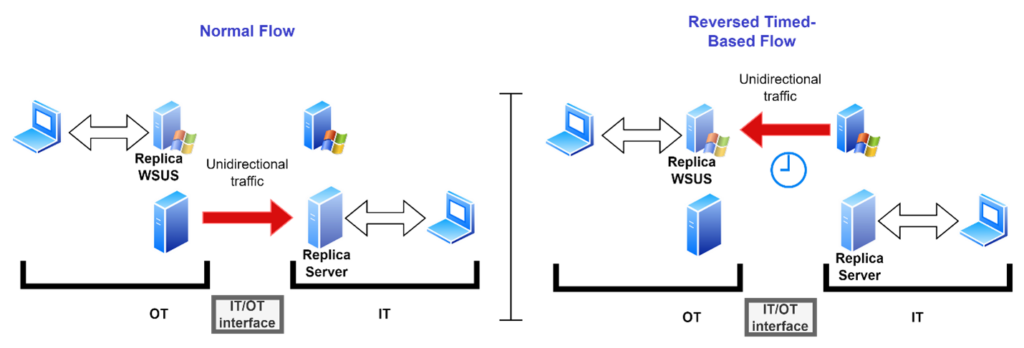
Time-based Unidirectional: Information is replicated outbound-only most of the time, but periodically the unidirectional device reverses orientation. Information and servers can be replicated outbound, or inbound, but never both simultaneously (the direction “flips”). In other words, outbound traffic is active for a certain percentage of the time, while inbound traffic is active for a different percentage.
A typical use case involves sending patches and production orders to the control system on a weekly basis. This is allowed only at specific times and solely in a unidirectional manner by transferring files from IT to OT. After the updates are transferred, the device physically reverses data flow direction again
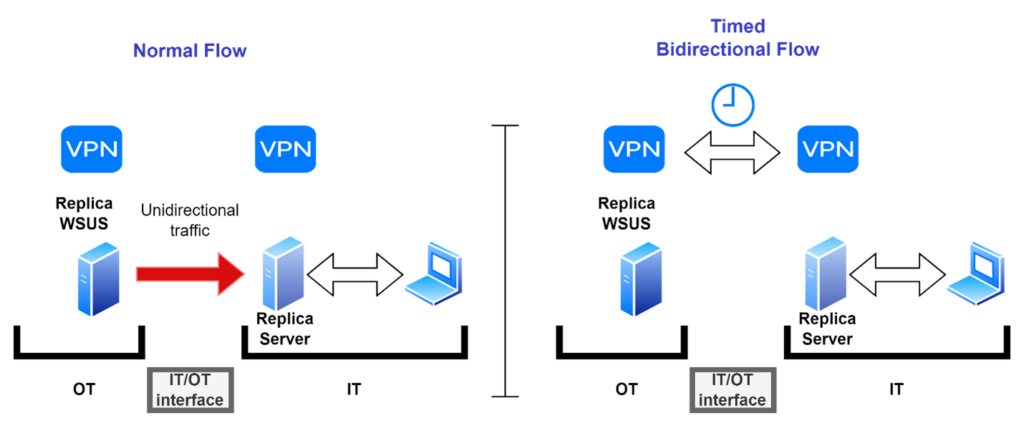
Time-based Unidirectional and Bidirectional: Information is continuously replicated unidirectionally outbound, but occasional bidirectional exchanges can be enabled at specific times or on demand. In this implementation, a temporary bidirectional data paths exists in parallel with the Unidirectional Gateway, usually terminating in a jump host.
A typical use case involves remote intervention by a vendor according to Service Level Agreements (SLAs). The vendor may require bi-directional remote connectivity for a short period of time. To enable that connectivity, personnel at the site turn a physical key to activate the bi-directional bypass unit for a pre-programmed period of time.
- Two Unidirectional Gateways: This approach decouples inbound and outbound traffic using two unidirectional gateways. Information and servers are replicated unidirectionally in both directions. It is important to note that this is different from having bidirectional traffic because the traffic does not generate a loop – application queries do not pass through one device with responses returning on the other – such a design would be no stronger than a firewall. The inbound and outbound Unidirectional Gateways each replicate servers – often different kinds of servers, in each direction.
A typical use case involves load balancing in power generation, where two separate Transmission System Operators (TSOs) want to exchange information about load while minimizing the risk of cascading a cyberattack across networks.
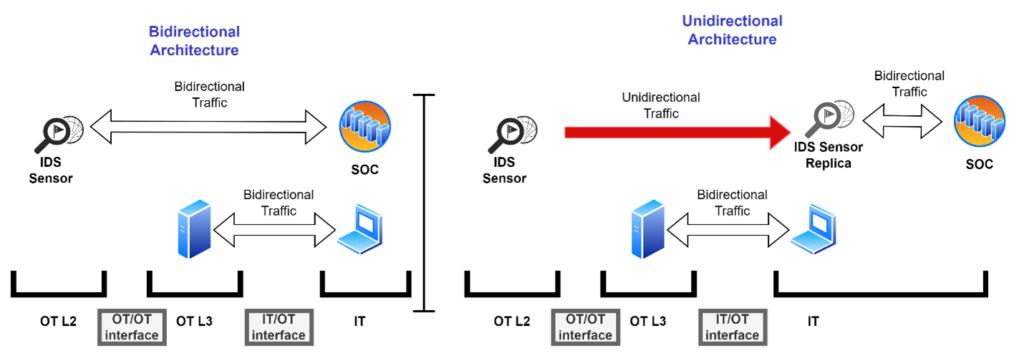
- Unidirectional ”Shortcut”: In this design, information from deep in a defense-in-depth industrial network must reach an external consumer, and it is impractical to send that information through normal layers of communications to the external consumer.
Use Cases: Industrial mirror ports may need to be replicated to IT-resident OT intrusion detection sensors. Mirror ports typically produce a lot of information and it may not be practical to send that volume of information from many mirror ports deep in an industrial network out through layers of networks to the IT network where the OT IDS sensors are. A second case – sending substation sensor information directly to the cloud without passing through the control center. This use case is currently being evaluated by the IEC committees overseeing the IEC62443 standard for transmitting data from Layer 2 to the cloud. The control center may still feature a firewall, but it is now less burdened, as most of the heavy data traffic is handled through the unidirectional gateway.
Conclusion
Unidirectional architectures offer significant benefits for the segmentation of OT networks and industrial systems, particularly in terms of security and reduced complexity. By replacing firewalls with unidirectional architectures, organizations can better protect their critical infrastructure from cyber threats. The various unidirectional architectures discussed, such as Pure Unidirectional, Time-based Unidirectional, Time-based unidirectional and bidirectional, two Unidirectional Gateways, and Unidirectional Shortcuts, provide different levels of security and flexibility based on specific use cases and requirements. These architectures allow for better isolation and control of data flows, which ultimately leads to improved security and reduced risk of cyberattacks in OT networks.
Moreover, unidirectional architectures can also help reduce the workload in higher-level networks in a defense-in-depth architecture, allowing them to focus on processing critical and time-sensitive traffic. This not only enhances the overall performance of the network but also simplifies network management by minimizing the number of data flows that must be supported through each network. As industrial systems continue to evolve and face increasingly sophisticated cyber threats, adopting unidirectional architectures will play a crucial role in maintaining the security and resilience of critical infrastructure.
For more details, see Waterfall’s guide: Unidirectional Gateways vs. Firewalls.
