Cyber Security in the Oil and Gas Industry
Cyberattacks of any kind to Oil & Gas facilities pose material threats to worker safety, environmental safety, public safety and, of course, continuous and efficient operations. For all these reasons, the industry in all its forms has for over a decade been a leader in deploying robust cybersecurity programs and technologies.
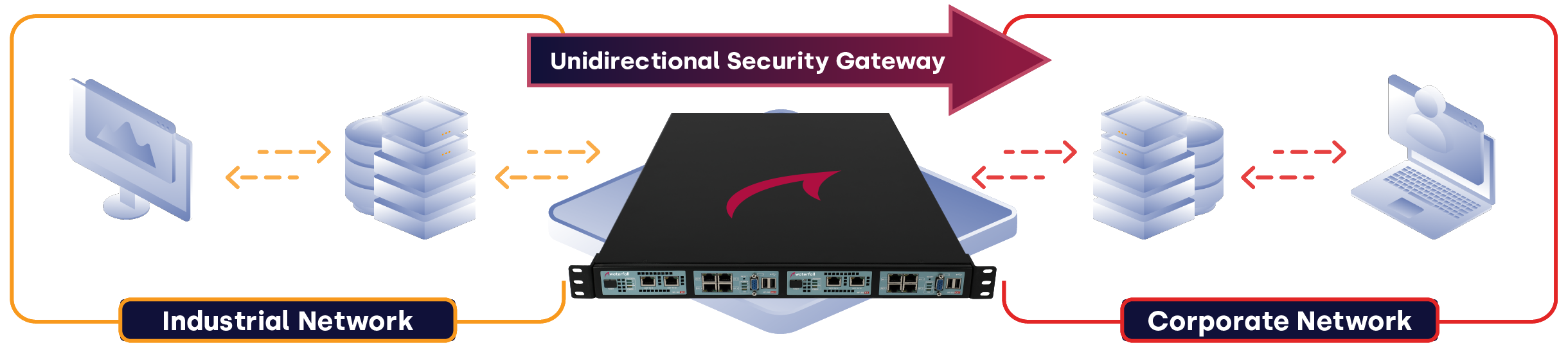
Waterfall’s unidirectional technology provides secure connectivity and remote access for the Oil & Gas industry throughout the supply chain, including upstream, midstream, and downstream.
Upstream
Cybersecurity programs must protect safe and efficient operations for all aspects of offshore platforms, as well as for more conventional sources of petrochemical feedstocks.

Midstream
Worker, environmental, and public safety are the top priorities for petrochemical pipelines. Protecting pipelines, tank farms, ports, and other facilities is the priority, with the goal of preventing any cyber sabotage that might lead to spills, ruptures, or outages at these critical infrastructures.

Downstream
Refineries are very large, expensive and complex infrastructures - cybersecurity programs must protect worker safety, public safety, environmental safety, while allowing continuous, efficient operations.

With Waterfall you get

Safe IT/OT Integration
Unidirectional Gateways provide business automation with access to OT / industrial data, without providing attackers or malware access to the industrial systems that are the sources of that data.

Safe Security Monitoring
Unidirectional Gateways provide enterprise and out-sourced Security Operations Centers (SOCs) with safe access to industrial network data, so generating utilities can leverage specialized expertise and economies of scale.

Secure Remote Access
Waterfall’s HERA® , Hardware-Enforced Remote Access, provides the functionality of remote access, without the inherent risks and threats that come with network connectivity.
Use cases
Business Automation
Undirectional Gateways replicate historians, databases, OPC servers and more to business networks. Business users and applications use the replicas normally – because all of the data that is allowed to be shared with IT networks is in the replica servers already.
Remote Access
Hardware Enforced Remote Access (HERA® ) enables remote management, updates, and troubleshooting for OT networks, safely. When software-based secure remote access is too great a risk, HERA® ‘s hardware provides remote functionality without the risks of remote connectivity.
Remote Vendors
Unidirectional Gateways safely replicate OPC servers, historians and other vendor systems for use by vendor cloud services, so that all players in these industries can benefit from specialized vendor expertise, and enable safe vendor remote access as needed, as well.
Offshore Platforms
Unidirectional Gateways provide unbreachable engineering-grade protection for drilling, ballast control, sub-sea operations and other vital aspects of offshore platforms, with high availability / no single point of failure options available when platform policies dictate.
Big Data Analysis
Unidirectional Cloud Gateways gather data from industrial / OT sources, convert the data into cloud-friendly protocols, and push the data through unbreachable unidirectional hardware out to the Internet and to vendor and proprietary cloud systems.
How it works

Connect
An industrial network safely to an IT network

Protect
The industrial network with hardware enforced technology

Replicate
Real-time operational servers to the enterprise IT network