ICS Cyber Security is Evolving
Industrial cyber security is changing. In response to this evolution, a discipline of ICS cyber security engineering is emerging. Cyber threats to industrial operations have become more capable, the consequences of actual compromises have become more dire, and the potential for unacceptable consequences in the future has become very real. Experts agree that this new discipline includes powerful tools for managing physical risks due to cyber attacks, tools that are unique to the OT / industrial automation space.
The emerging discipline of ICS cyber security engineering and examples of the organizations supporting it, are documented in a new report from Waterfall Security Solutions: Emerging Consensus for Industrial Security Engineering. In this report we look at recent trends in the industrial security field, review security engineering measures that governments, standards, and insurers are increasingly demanding, and we interpret what this means for corporate governance and due care. Expectations have changed – risk managers, enterprise security teams and engineering teams need to track and keep up with this emerging consensus.
Modern Threats
The industrial security threat environment continues to worsen. Figure (1) shows cyber attacks over a twelve-year period – attacks that brought about physical consequences in process and discrete manufacturing industries.
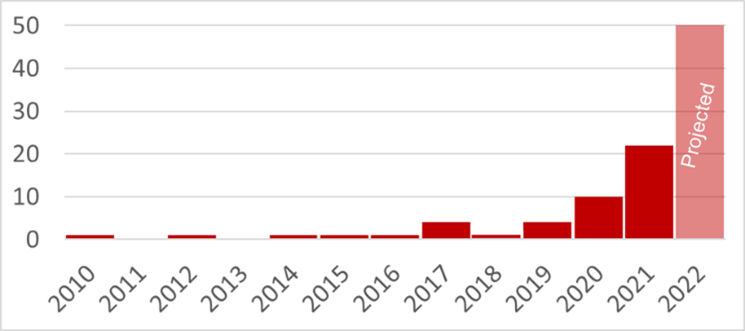
Today, deliberate attacks with physical consequences are more than doubling annually. Most of these attacks are ransomware. In 2020, ransomware criminal groups discovered how to monetize attacks on industrial operations and have been scaling up their operations ever since. The report delves into greater detail as to what certain analysts predict the threat landscape trends look like over the next 3 to 5-year period.
What is ICS Cyber Security?
This evolution of the cyber threat environment in the industrial sector is driving a corresponding evolution in industrial security best practices. Consensus as to the nature of IT vs. OT security is evolving as well.
In OT environments we need first and foremost to protect safe physical operations from attack information, not protect the information itself. The second priority on most networks, and especially critical infrastructure networks, is not to protect information or protecting access to information, but to protect reliable physical operations first and foremost.
All industrial security standards, old and new, agree that certain security practices in OT networks must differ from standard IT practices in several ways:
- Engineering change control practices mean that security updates often cannot be applied promptly,
- The cost of safety certifications means that old versions of operating systems can be very difficult to replace, and
- Even basic security tools such as anti-virus systems and per-user passwords cannot be applied universally
The modern consensus is that these differences are superficial, and that the fundamental difference between IT and OT networks is found in worst-case consequences of compromise. The report elaborates on standards from NERC CIP, ANSSI others of definitions of network classifications and consequences of compromise. The bottom line: the essential difference between IT and OT networks is that human lives, damaged equipment, environmental disasters, and public safety impacts cannot be “restored from backups.” This means that IT and OT networks must be managed very differently.
ICS Cyber Security Engineering
The essential difference between engineering and cybersecurity approaches to cyber threats is predictability. In contrast, enterprise Security Operations Centers (SOCs) assume that their networks have been compromised and thus set about systematically searching for and detecting compromised equipment, and then responding to the intrusion and recovering that equipment to an uncompromised state. When applying this methodology to OT networks, we hope to detect, respond and recover in time – before unacceptable consequences are realized. This is the essential difference between IT-centric security and security engineering – engineering must be predictable. “Hope” is not good engineering.
This is why a crucial part of the emerging ICS cyber security engineering discipline is network engineering – designing networks to outright eliminate important classes of cyber threats. The report outlines several examples of engineering network designs that do just that.
Unidirectional Gateways
By far the most common example of network engineering is the use of unidirectional gateway technology. Unidirectional gateways are deterministic. The US NIST glossary defines:
“Unidirectional gateways are a combination of hardware and software. The hardware permits data to flow from one network to another but is physically unable to send any information at all back into the source network. The software replicates databases and emulates protocol servers and devices.”
Unidirectional gateways are deterministic, meaning that they are physically able to send information in only one direction. The gateways are deployed almost exclusively at the IT/OT interface, sending information from industrial automation systems out into business automation systems, so that those business systems can use the OT information to realize business efficiencies.
Modern standards increasingly recommend that unidirectional gateways be deployed at consequence boundaries – boundaries between business networks and networks where worst-case consequences of compromise could result in unacceptable threats to worker or public safety. The report looks closer into the specific examples of unidirectional advice from organizations around the world responsible for issuing guidance for industrial and critical infrastructure sites.
Unidirectional gateways are also used increasingly when, even in the absence of risks to public safety or to the environment, a production outage due to a cyber attack would materially impair earnings or the reputation of a business. In this case, the engineering decision to deploy the unidirectional gateway is more a business and financially motivated decision than a safety-motivated one. When the cost of the gateway is dwarfed by the cost of a production outage, the risk-reduction ROI for deploying the gateway is very simple.
Due Care
Due care, also known as ordinary care or reasonable care, is defined by governments, courts, and insurers as the standard of care that any reasonable person would exercise in the same situation or under similar circumstances. Government, legal and insurance expectations for due care are changing rapidly. Part of this is due to the deteriorating threat environment.
Expectations are also changing as insurers become aware of powerful ICS cyber security engineering techniques to eliminate entire classes of cyber risk. In short, insurers, governments, and the courts increasingly expect all practitioners charged with managing cyber risk to exercise due care – to have evaluated and applied all appropriate best practices and affordable, widely-available risk mitigation approaches and technologies, including the emerging techniques of security engineering.
Conclusion
The emerging consensus for industrial cybersecurity engineering is coming in the context of a steadily deteriorating cyber threat environment. Governments, standards, and experts agree – the time has come for adding deterministic, unbreachable engineering approaches for managing cyber risk to our existing information-centric ICS cyber security programs. In particular, unidirectional gateways deployed at consequence boundaries, most commonly the IT/OT interface, have emerged as very important network engineering tool for protecting and ensuring the reliable operation of our industrial facilities.
To see the full Emerging Consensus for Industrial Security Engineering report, click here>>
