Cybersecurity In Mining
Protecting Mining Operations From Evolving Cyber Threats

Customer/ Partner:
Australian-based surface and underground metals mine.
Customer Requirement:
Enable safe and secure replication of data from the critical network to the enterprise network. Monitor critical network screens in real-time and access the critical network in a controlled way.
Waterfall’s Unidirectional Solution:
Secures control system network perimeters from external threats with hardware-enforced Unidirectional Security Gateways, enabling enterprise-wide visibility for operations status and
monitoring data.
Cyber Threats To The Mining Industry
Increasing digitalization and automation of the mining industry improves the safety of miners, reduces costs, and promotes operational efficiencies. However, these improvements can also expose interconnected mine control systems to remote manipulation and sophisticated cyber-attacks such as targeted ransomware. Today’s mines need to stay safe in a steadily worsening cyber threat environment.

The challenge
Enable safe visibility of operational data from the mine’s operational network in the enterprise network. In addition, monitor the screens of critical operations workstations in real time, without incurring cyber risks to continuous, correct and efficient mining operations. Modern mining operations employ a wide range of sensors and equipment to safely extract ore, transport it to processing plants and process the minerals or metals from the ore. Protecting these mission critical operations with only software firewalls not enough in today’s threat environment, because all software can be compromised.

Waterfall solution
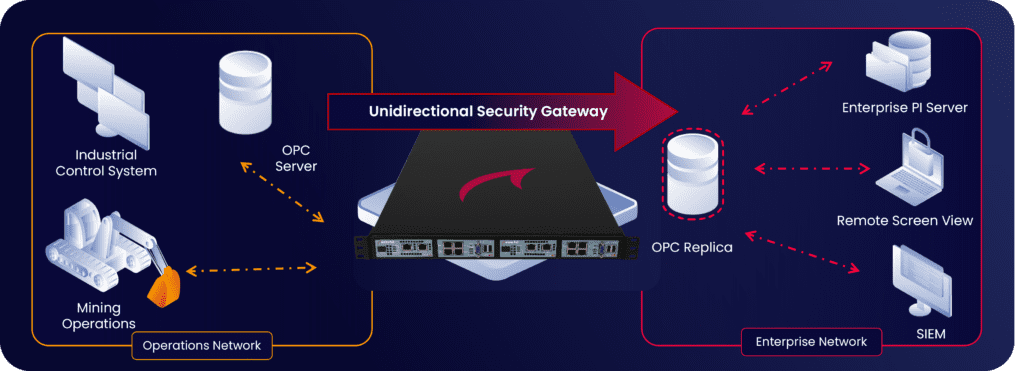
A Waterfall Unidirectional Security Gateway was installed between the mining control system and the enterprise network. Unidirectional Gateway software replicates an OPC server and a Syslog Server from critical control networks to the enterprise. Enterprise clients interact normally and bi-directionally with the replicas. In addition, a Waterfall Remote Screen View connector was deployed, enabling users on the enterprise networks to monitor screens in the shaft network.
Results & benefits
Security: The operations network is now physically protected from cyber threats emanating from external, Internet-exposed networks.
Visibility: Enterprise users and applications can see all operations data that is authorized to be shared with the enterprise network. Waterfall’s Unidirectional Security Gateways provide access to critical operations data without providing access to critical mining systems.
Compatibility: Enterprise users and applications access the replicas seamlessly and bi-directionally. Unidirectional Gateways are plug-and-play replacements for firewalls.

Theory of Operation
Waterfall Unidirectional Security Gateways replace firewalls in OT network environments, providing absolute protection to control systems and industrial control networks from attacks emanating from external less-trusted networks. Waterfall Gateways contain both hardware and software components. The gateway hardware is physically able to transmit information in only one direction – out of the control and shaft networks to enterprise and Internet networks. The gateway software replicates servers and emulates devices. External users and applications use the replica systems normally and bi-directionally. Waterfall products enable deep visibility into operations data and operations networks for enterprise users and systems, as well as for Internet-based websites, applications, and cloud service providers. With
Waterfall products deployed, such visibility is safe from attacks originating on these external networks because of the physically unidirectional nature of the gateway products. Waterfall Unidirectional Gateways and related products provide safe access to mining and shaft data, without providing access to control critical systems

Unidirectional Security Gateways Benefits:
![]() Safe, continuous monitoring of operations networks from enterprise-managed, central platforms
Safe, continuous monitoring of operations networks from enterprise-managed, central platforms
![]() Strong physical protection for mining processes, reliable and quality production, and personnel safety
Strong physical protection for mining processes, reliable and quality production, and personnel safety
![]() Safe remote supervision of changes to protected systems Central enterprise security and performance monitoring for OT networks and applications
Safe remote supervision of changes to protected systems Central enterprise security and performance monitoring for OT networks and applications
![]() Real time OPC data is available to business network users and applications via the enterprise historian
Real time OPC data is available to business network users and applications via the enterprise historian
![]() Eliminates risks to reliability, worker safety, and public safety due to external cyber attacks
Eliminates risks to reliability, worker safety, and public safety due to external cyber attacks
Share
Trending posts
Waterfall Security Solutions recognized by Gartner®
How to Apply the NCSC/CISA 2026 Guidance
Stay up to date
Subscribe to our blog and receive insights straight to your inbox