Air gaps are confusing – a significant minority of practitioners use the term “air gap” in a way that is very different from how everyone else uses the term. In the words of the immortal Indigo Montoya in The Princess Bride:
“You keep using that word. I do not think it means what you think it means.”
Confusion around the term “air gaps” can lead to serious mistakes for industrial cyber risk management.
What should the word mean? Historically, an air gapped network was one with no online data connection to any other network – no serial connections, no network connections, no wireless, no fiber, nothing. The only way to get information into an air gapped system or network was offline transfers – by physically carrying the data into the network on cell phones, USB drives, DVDs and CDs, or more realistically in the day, on floppies and magnetic tape.
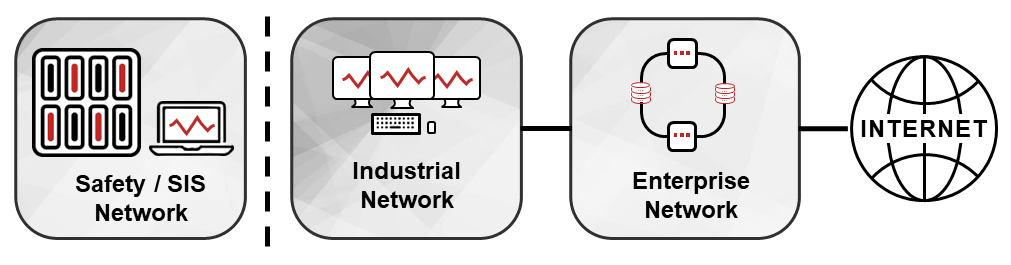
This kind of air-gapped industrial network largely disappeared in the late 1990’s when most industrial enterprises started their process of IT/OT integration – the process of connecting industrial data sources into company-wide engineering platforms and business automation platforms, for example the SAP Enterprise Resource Planning (ERP) systems that a great many businesses were deploying at the time. That these networks disappeared long ago is often lost on older managers and business leaders who started as engineers even longer ago, and today have not looked hard at a network diagram in 20 or 30 years. Such managers sometimes still insist that their industrial networks are air gapped, and therefore need minimal additional cybersecurity measures. They are of course wrong – modern industrial networks are almost universally connected to external networks, often in a great many ways. For example, all too often industrial equipment vendors will install DSL lines or other Internet connections directly to their equipment while installing their gear at a site. These vendors will even pay the telecoms provider for these connections, making these connections almost entirely invisible to industrial organizations.
Again, almost nothing is “truly” air gapped any more. Correcting “old school” business leaders who still think otherwise takes a bit of tact, and when corrected, the need for cybersecurity measures becomes clear to everyone – you would think.
Pivoting & Daisy-Chained Attacks
Unfortunately, there is a substantial minority of practitioners who use the term “air gap” a different way. I was on a webinar a couple days ago where the CISO of a critical infrastructure provider described his industrial networks as air-gapped. After the initial shock wore off, it became clear from context that the CISO meant that most of his industrial networks had no way to route an Internet Protocol (IP) packet directly to the Internet. Firewalls on the networks would permit industrial sources to send packets to destinations in the IT network, but not to Internet destinations through the IT network.

These modern practitioners may think that “air gap” is a nice shorthand for “not Internet-routable,” but this shorthand is a problem. Use of the term this way has led to serious errors in risk management. For example, modern ransomware uses targeted attack techniques. The criminal group might deceive an enterprise user into clicking on a malicious attachment and compromising their computer. That computer connects to a command-and-control (C2) center on the Internet and the criminal group then pivots the attack – operates the compromised enterprise computer by remote control to extend their attack deeper into the enterprise network.
The industrial cyber risk question? Can that remote-control attack be extended into the industrial / OT network? In a truly air gapped industrial network (if you can find one), the answer is “no.” There is no online connection of any sort into a truly air gapped network, like the SIS network in Figure (1). There is no online connection that allows any sort of remote control attacks.
But – in a network like the one in Figure (2) – where IP packets can be exchanged between the enterprise and industrial networks, but not directly between the Internet C2 and the industrial network, yes, remote-control attack can propagate into the industrial network. How? The attacker pushes the malware to the industrial network over a file share or some other means and configures the malware to connect to a compromised machine on the enterprise network for attack instructions, not to the Internet C2. Attack commands from the C2 and responses to the C2 are daisy chained in this example, through compromised computers on the enterprise network.
“Air Gaps” Mess Up Industrial Security
How does this mess up risk management? The CISO tells the board and other business leaders, “don’t worry, our industrial network is air gapped.” Those people might push back and ask, “Are you sure? I was told that air gaps pretty much disappeared 25 years ago.” The CISO replies confidently “Nope – I’ve verified it with our technical people – our industrial networks are truly and absolutely air gapped.”
Of course, what the CISO means is, “our industrial networks cannot send messages directly to the Internet, but they can send messages to compromised equipment on our enterprise network.” What the other business leaders hear is, “there is no way at all for attack commands from an Internet-based C2 to reach our industrial networks.” This latter interpretation is a serious mistake when it leads those leaders to reduce or delay funding for industrial cybersecurity programs.
Stop Using the Term “Air Gaps”
In the modern world, almost nothing is air gapped in the original sense of the word, except for maybe some Safety Instrumented Systems, and the occasional CPU on a power drill, saw or other power tool. Security practitioners who use the word “air gap” to describe their connected networks are sowing confusion. Stop it.
If your industrial network can connect only to hosts in a DMZ, and your DMZ hosts can connect only to enterprise hosts, and vice-versa, say that your industrial and DMZ firewalls are “deny by default” or “have outbound access control,” not that your networks are air gapped.
