During 2021, the number of cyber attacks giving rise to physical consequences in manufacturing and process industries more than doubled over those reported in 2020. Almost all these attacks were the result of targeted ransomware and impacted multiple sites.
These findings and others are documented in a new report: OT Security Incidents – 2021 Trends and Analyses, a cooperation of ICSSTRIVE and Waterfall Security Solutions. The data in the report comes from the new icsstrive.com OT cyber incident database. The database records and categorizes public reports of OT incidents.
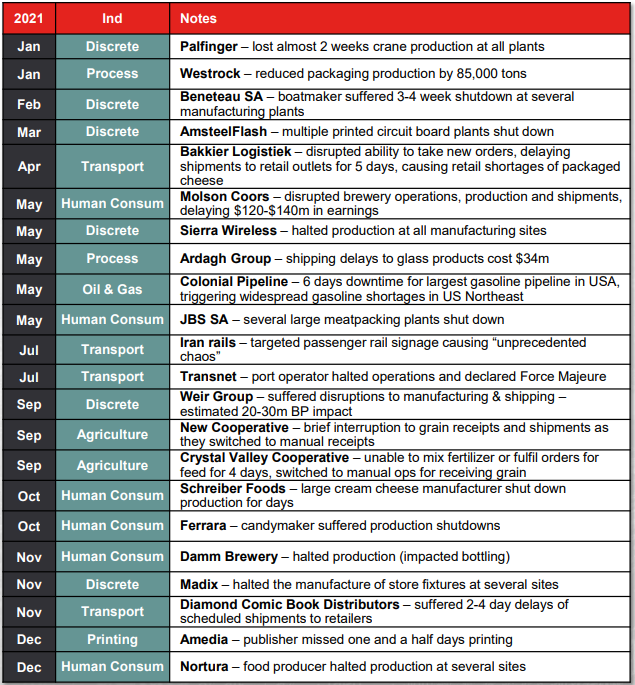
2021 OT Outages
Of 64 incidents reported in discrete manufacturing and process industries, 22 were cyber attacks with physical consequences. These attacks represent a 144% increase over such incidents in 2020.
Ransomware was involved in all but one of these incidents: the July rails incident in Iran. OT ransomware incidents with physical consequences have thus increased 133% year-over-year from 2020 (from 9 to 22). Most of these attacks impacted multiple sites. Published estimates of damage ranged up to $140m per incident.
In most of these attacks, IT assets were reported to be impaired, while a minority of attacks manipulated or impaired OT assets directly. The Colonial Pipeline incident is an example where IT assets suffered the ransomware attack, but the company decided to shut down all operations out of an abundance of caution.
Industries
World-wide, both IT and OT networks in petrochemicals industries have a reputation for being heavily defended, and so it makes sense that there was only a single incident in those industries with physical consequences – the Colonial Pipeline attack.
In transportation, some OT networks also have a reputation for being thoroughly protected, for example passenger rail signalling systems. Thus, the comparatively large number of incidents in transportation does seem surprising. Not all incidents in transportation were in passenger rails, however, and those that were targeted the more exposed ticketing and signage systems rather than the more heavily protected signalling systems.
The ICSSTRIVE database also reports four attacks on water and wastewater facilities in 2021. While the worst consequences of these attacks resulted in only “near miss” categorization, the water sector is traditionally underfunded for cybersecurity. This is an issue, considering the importance of what the sector produces – clean drinking water for citizens.
Cloud-Seeded Attacks
Another conclusion in the report concerns cloud-connected industrial infrastructure. In July 2021, a ransomware group exploited a Kaseya cloud service to distribute ransomware to over 1000 organizations in the space of 45 minutes. No impacts on process or discrete manufacturing industrial operations were reported, though 500 grocery stores in Sweden shut down for two days because their cash registers were crippled.
The report predicts that within two years, we will see this class of attack extend into industrial operations, with physical consequences. That is: ransomware actors or other
threat actors will distribute malware to hundreds of industrial sites simultaneously in the form of software or firmware updates.
Ransomware Details
Data from both 2020 and 2021 suggests three ways that ransomware can cause physical consequences in process and discrete manufacturing industries:
- Ransomware actors can target OT systems directly, through targeted or supply-chain attacks, resulting in impaired OT automation and operations,
- Ransomware actors can target IT systems, indirectly affecting OT systems when victim enterprises shut down physical operations “in an abundance of caution,”
- Ransomware actors can target and impair IT systems that are essential to live industrial operations.
Prudent enterprises must take steps to eliminate the possibility of all three kinds of OT shutdowns due to ransomware attacks.
Recommendations
The top objective of an OT security programme with the intent to survive a cyber incident is continued and reliable operations throughout the incident. IT networks are much more exposed to ransomware attacks than OT networks should be, so it is reasonable to expect that IT networks will be breached much more frequently than OT networks. Thus, for many industries, automation must be designed so that operations can continue running safely and continuously, even when the more-exposed IT network is compromised.
Secure Operations Technology (SEC-OT) is the methodology used by the most secure sites to achieve this goal of safe, continuous and correct operation. SEC-OT sites manage attack information flows so thoroughly that the movement of attack information into operations networks, either deliberately or accidentally, is practically impossible. With strong SEC-OT protections in place, such as removable media controls, removable device controls and unidirectional gateway technology, ransomware attacks cannot reach the industrial control systems operating physical infrastructures and manufacturing processes, and so cannot cause the malfunction of these processes.
Controlling dependencies on cloud services deserves special mention. Ransomware delivered through cloud services can cripple not just one factory or physical operation, but all operations that use the compromised cloud service. Preventing such compromise is straightforward – secure sites can enjoy the benefits of industrial cloud services, safely, by connecting to those services only via hardware-enforced unidirectional gateway technology.
Conclusion
Ransomware and other cyber attacks that shut down or otherwise impair physical operations are increasing at a rapid pace. Worse, today’s ransomware groups are trailing nation-state attack tools and techniques by only about half a decade. What we see the nation states doing to each other today, we should expect ransomware criminals to be doing to all of us in less than five years. For example, the report predicts that within the next 2-3 years, cloud-seeded ransomware and two-factor authentication bypass attacks will pose very serious threats to critical infrastructure organizations and to manufacturers of all types.
In 2021 the world saw 22 attacks with physical consequences documented in the popular press for process and discrete manufacturing industries. Every one of these attacks defeated conventional IT-grade security measures. If we wish to avoid our physical operations being crippled by attacks on our IT networks, then we need stronger protection.
To Dig Deeper
To see the full threat report, visit the ICSSTRIVE website. For the latest news on industrial safety and security, please visit Industrial Safety and Security Source or subscribe to the weekly The Shield newsletter.
