Engineering risk management is part of industrial operations and automation systems to different degrees, legitimately so, and the degree of engineering involvement is very important when selecting an OT security vendor for a given site or set of sites. Safety engineering, protection engineering and other engineering disciplines, for example, will be much more intensely involved with a large power plant or railway switching system, than they are for a small shoe factory.
When selecting OT security vendors for either service provider or technology provider roles, it is important that we align vendor specialization and capabilities with the way our organization and industrial site are managed. The security approach we select will be somewhere in the spectrum from engineering/OT-focused to enterprise/IT-focused. Understanding our organization’s risk tolerance and the consequences we face at each site in a worst-case outcome of a cyber attack will determine our approach to cybersecurity. Once that is established, we can narrow down our short list of vendors to align with our risk profile and approach.
What is OT Security
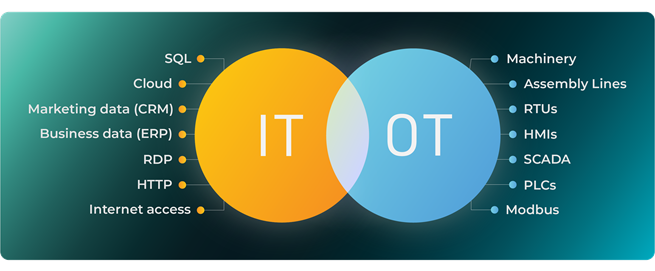
OT security protects operational technology systems used in industrial environments from cyber threats. It secures critical infrastructure like manufacturing, energy, and transportation by controlling physical processes through secure network segmentation, device hardening, and continuous monitoring.
Addressing Risk Before Choosing an OT Security Vendor
A bit of background – the practice of managing risk while seizing opportunities in pursuit of business objectives, otherwise known as enterprise risk management, is a discipline that requires mitigating multiple risk exposures. For industrial sites, managing enterprise risk involves an added focus on cyber risks to physical operations. If the responsibility for OT security management resides with the CISO, engineering decision makers still must be heavily involved in the process of securing our sites, because it is those practitioners who are primarily responsible for protecting safe, reliable and efficient physical operations from a wide spectrum of non-cyber risks. This is because the tools and techniques used by engineers to manage physical risks and and those used by cybersecurity practitioners to manage cyber risk can interfere with each other.
Historically, industrial control system vendors were selected by engineering teams. ICS vendors were selected based on their ability to design and implement solutions to integrate into an existing automation system to achieve a business goal, without presenting additional risk (operational or safety) to current processes. If the consequences to any kind of mistake – errors and omissions – were considered unacceptable, the engineering team would become intensely involved in designing and evaluating the risk of every change to the control system. All change has risks, and so must be engineered. Today, the interdependent elements of most industrial sites are physical, human and cyber. Engineering and enterprise teams must be aligned in both security approach and understanding of worst-case consequences to address this connectivity risk; it is a critical first step in selecting an OT security vendor to meet business objectives. Below are 4 steps to make sure the OT security vendor you select is the right fit.
1. Where Does Our Site Fit on the IT / OT Security Spectrum?
In industrial enterprises, there can be disagreements between engineering teams and enterprise security teams as to how to pursue OT cybersecurity. In the past, cybersecurity was managed by the enterprise security team, with control system security largely neglected. Industrial cybersecurity was a blind spot for enterprise security teams, because all aspects of the design of industrial systems was the responsibility of engineering teams. Cybersecurity was a “blind spot” for engineering teams, because the engineering profession historically had little awareness of cyber threats to operations. Today connectivity and business automation reach deep into control networks, allowing increased visibility, data collection and business efficiencies, but also increased opportunity for attacks to infiltrate networks able to bring about material and unacceptable physical consequences when sabotaged.
From the engineering/OT perspective, classic IT security measures such as anti-virus and security updates introduce change (sometimes far-reaching change) to the control network. These and other classic IT cybersecurity measures fly in the face of the classic engineering imperative to control unacceptable risks by controlling change. To engineering teams, the constant stream of changes introduced by IT approaches to cybersecurity introduce and increase risks of physical malfunction, risk the security program is supposed to be reducing; the cybersecurity cure causes more outages than the cyber risk disease.
In the railway switching system example, many kinds of engineering teams will be deeply involved in managing risks to public safety and to equipment, often by using an engineering change control system that is extremely strict. In a small shoe factory, safety and equipment damage concerns are much smaller, and are often mitigated thoroughly by employee procedures and mechanical equipment or electric power lock-outs to immobilize machines and robots while under repair. When selecting an OT security vendor, determining where our industrial site(s) fit in terms of the intensity of involvement of engineering teams is an important first step.
2. Framework Pillar Prioritization
The next step is one of aligning the degree of engineering involvement with approaches to cybersecurity, often using the terminology of the pillars in the NIST Cybersecurity Framework.
The NIST Framework consists of 5 principal mitigation areas or “pillars” called: Identify, Protect, Detect, Respond and Recover. These 5 cybersecurity pillars at a very high level address the questions: What processes and assets need protection? What are the appropriate safeguards to ensure protection of the assets? How can we identify the cyber incidents and attacks? How can we contain the impacts of cyber events? And finally, what are the processes in place to restore capabilities and services impacted by a cyber event?
These pillars represent a comprehensive framework or checklist, but do not purport to be prescriptive. Organizations must interpret and apply the framework in accordance with their own risk profile. In the industrial context, our understanding of what kind of OT security provider we need starts by understanding our worst-case consequences of a cyber incident.
Every site is different. In our earlier railway vs shoe factory example, a rail switching malfunction could result in immediate and severe safety and public safety consequences. A cyber attack that causes the shoe factory control system to malfunction, in contrast, generally results in only business consequences. The worst damage a cyber attack may cause to our shoe factory automation system is likely to be only a short operational outage plus clean-up costs, often pulling in external contractors on an emergency basis.
We must then compare these worst-case consequences to the risk tolerance of our organization as expressed by our board of directors and senior executives and select which pillars of the NIST Framework to prioritize to greater and lesser extents. For example, public safety impacts most often are categorized by the board as unacceptable consequences – which means the rail operator would emphasize the protect pillar in the NIST framework, to prevent these impacts. Modest business interruptions, however, may be comparatively acceptable business impacts, in which case the shoe factory might choose to emphasize the detect, respond and recover pillars, as is characteristic of IT-centric enterprise security programs. A mature OT cybersecurity program uses all of the NIST pillars to some degree, but businesses with truly unacceptable worst-case consequences of compromise tend to prioritize the protect pillar more than the detect, respond and recover pillars.
3. Different Vendors Focus on Different Pillars
When selecting OT security vendors, we need to understand that very often no single vendor can address all of the 5 pillars equally. Some vendors will be specialists in network detection techniques and technologies, some will have advanced expertise in incident response, and others will offer protection designed for addressing engineering risk. Firewalls and whitelisting technologies for example, are more aligned with the protect pillar, while asset inventory management aligns with the identify pillar, and backups and tested “rebuild completely from known-good media” tools and procedures align with the recover pillar. To be most effective at our sites in our organization, an OT security vendor should have a proven track record in delivering on the NIST pillars our organization and site(s) prioritize.
4. Security Vendor Familiarity with ICS
To be effective in securing an industrial control system, an OT security vendor must also be familiar with industrial automation systems and their relation to conventional cybersecurity technologies. In the shoe factory example, the business has most likely selected a classic IT-style prioritization on the detect, respond and recover pillars. Selecting an OT security vendor that is heavily focused on the “protect” pillar and on engineering change control systems for the shoe factory is likely to result in a costly and over-designed security system focused on preventing all compromise at almost any cost. On the other hand, any OT security vendor installing any solution for the shoe factory should still demonstrate a knowledge of the site’s automation systems that is deep enough to design the intrusion detection and security monitoring rules and solutions that are able to detect attacks in progress on automation systems and automation communications.
More importantly, in the large power plant or rail switching example, an OT security vendor must demonstrate a much deeper understanding of the industrial automation and industrial security domain. A vendor, in this circumstance, should have a deep understanding of engineering change control imperatives, as well as of compensating measures and alternative approaches to addressing OT cyber risk when conventional IT security approaches are poor fits. A deep understanding of the intrinsic limitations of control system functionality, vendor support agreements, warrantees and many other aspects of control systems design and operation are other examples of important attributes of a “protect” focused vendor.
Choosing an OT Security Vendor – Recap
Different industrial process and automation system designs have different worst-case consequences of compromise, and different organizations have different tolerances for cyber-induced consequences. Sites and organizations where worst-case consequences are considered unacceptable tend to have engineering teams that lean heavily on engineering change control processes, while other sites and organizations may use more IT-style processes and systems to manage their industrial automation. To select an OT security vendor likely to perform effectively in each circumstance means we must:
- Understand our consequences and risk tolerances,
- Use that understanding to decide how we want to prioritize the pillars of the NIST Framework,
- Find an OT security vendor with the demonstrated ability to emphasize the pillars we need emphasized, and
- Ensure that the vendor we select knows enough about the physical processes, automation, and engineering management disciplines that we are using at the sites we need the vendor to secure.
A vendor who secures all industrial sites with a one-size-fits-all approach is a recipe for failure, even more so if that one-size approach is a vanilla IT-centric approach, which is a poor fit for pretty much all industrial sites.