When you’re protecting operational technology infrastructure, the security solution you pick could mean the difference between weathering a cyberattack and making headlines for all the wrong reasons. It’s not really about whether you need protection anymore; that ship sailed when hackers started going after power grids and water systems. What matters now is figuring out which technology will actually work when attackers come knocking.
OT security isn’t your typical IT problem. We’re talking about systems that run power plants, manage water treatment facilities, control manufacturing lines, and keep transportation networks moving. When these systems fail, you’re not dealing with stolen passwords or leaked documents. You’re looking at potential physical damage, environmental disasters, or genuine public safety threats. Understanding your security options has never been more critical.
Two technologies dominate the conversation when it comes to creating secure boundaries between OT networks and external threats: data diodes and firewalls. Both handle security, but their approaches are worlds apart. This choice shapes everything: immediate protection, operational flexibility, compliance posture, and how well you’ll handle whatever new threats emerge.
TLDR: Data Diode vs Firewall key differences:
| Aspect | Data Diode | Firewall |
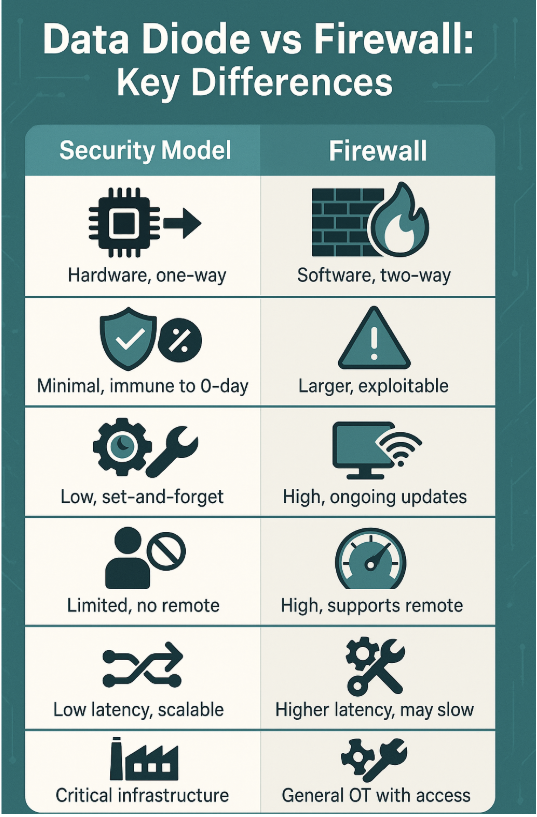
| Security Model | Hardware, one-way | Software, two-way |
| Attack Surface | Minimal, immune to 0-day | Larger, exploitable |
| Maintenance | Low, set-and-forget | High, ongoing updates |
| Flexibility | Limited, no remote | High, supports remote |
| Performance | Low latency, scalable | Higher latency may slow |
| Compliance | Simple, physical proof | Complex, ongoing checks |
| Use Cases | Critical infrastructure | General OT with access |
What is a Data Diode? Core Technology and Functionality Explained
A data diode is a cybersecurity device that enforces one-way data transfer between two networks. It allows information to flow out of a secure system without allowing external data to flow back in. Organizations use data diodes to protect critical infrastructure, defense systems, and industrial control networks from cyberattacks.
The technology works by physically severing the return path that network communications typically need. Regular network connections require two-way communication for protocols like TCP/IP to work properly. Data diodes break this requirement at the hardware level, making it physically impossible for external systems to establish connections or push data back into protected networks.
What is The Technical Architecture of Data Diodes?
The hardware creates what’s essentially an air gap with controlled, one-way data transmission. Inside these devices, fiber optic connections carry data from OT networks to external monitoring systems, but the physical design prevents signals from traveling backward. The transmit fiber literally can’t receive signals, and the receive side can’t transmit anything. This isn’t a software setting that could accidentally get changed; it’s baked into the hardware design.
Your OT systems still provide all the data needed for monitoring, reporting, and analytics. Historians keep collecting process data, SCADA systems continue displaying real-time information, and operators maintain full operational visibility. The key difference? This visibility never creates a pathway for attackers to reach critical systems.
Data diodes also eliminate concerns about network protocols being exploited. Since there’s no return communication path, traditional network-based attacks simply can’t function. Malware that depends on command and control communications finds itself cut off from its handlers. Remote access trojans lose their ability to communicate back to attackers.
Security Guarantees Provided by Hardware Enforcement
Hardware enforcement gives you security guarantees that software simply can’t match. With a data diode, protection doesn’t depend on perfect configuration, timely updates, or hoping that nobody’s found an undiscovered vulnerability. The security model is binary: data goes out, nothing comes back.
This approach eliminates entire categories of cyberattacks that need two-way communication to succeed. Advanced persistent threats, remote access trojans, and command-and-control communications all need bidirectional connectivity. By physically preventing this connectivity, data diodes create an impenetrable barrier.
The reliability extends beyond just cybersecurity threats. Data diodes also protect against insider threats who might attempt to establish unauthorized network connections. Even with administrative access to systems, an insider can’t override the physical limitations of the hardware.
Firewall Technology in OT Security Contexts
Firewalls have evolved considerably since their early days, particularly for operational technology environments. Modern OT firewalls include deep packet inspection, protocol-aware filtering, and specialized capabilities for industrial communication protocols. They act as intelligent gatekeepers, examining traffic and deciding what gets through based on predefined rules and policies.
Unlike data diodes, firewalls keep bidirectional connectivity alive while trying to filter out malicious traffic. They analyze packet contents, addresses, protocol types, and application behaviors to determine whether communications should pass or get blocked.
Evolution of Firewall Technology for Industrial Networks
Firewalls were originally built for IT networks, where the main job was to keep malicious traffic out of corporate systems while still allowing employees, servers, and applications to connect to the internet. These early firewalls were not designed with operational technology (OT) in mind. Industrial networks have very different requirements-24/7 uptime, specialized communication protocols, and devices that often remain in service for decades. Applying traditional IT firewalls directly to OT environments often caused disruptions, latency, or outright failures because the firewalls simply didn’t “understand” how industrial equipment communicated.
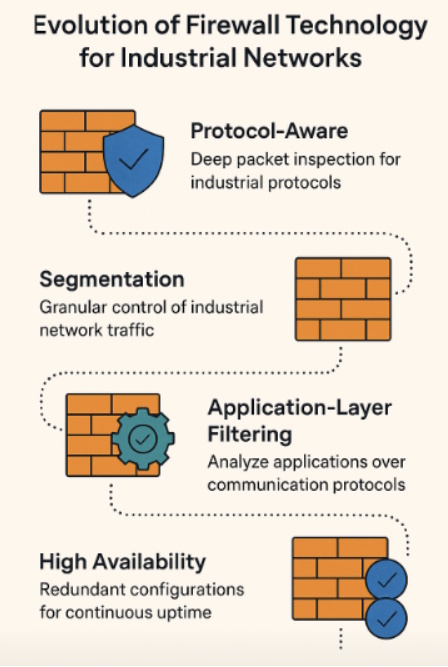
To meet these unique demands, firewalls for industrial use evolved in several key ways.
First, they became protocol-aware. Industrial control systems rely on communication protocols such as Modbus, DNP3, IEC 61850, OPC, and PROFINET. Unlike typical IT protocols, these are highly specialized and often lack built-in security features. Modern OT firewalls now include deep packet inspection (DPI) for these protocols, meaning they can read and interpret the actual commands and values being exchanged between devices. This allows the firewall not only to block generic suspicious traffic, but also to detect anomalies such as unauthorized control commands or malformed data packets that could indicate tampering.
Second, OT firewalls added segmentation capabilities tailored to industrial environments. In IT, segmentation often means dividing a corporate network into different security zones. In OT, segmentation is even more critical because it can stop a compromise in one part of a plant or facility from spreading to safety-critical or production-critical systems. Modern industrial firewalls enable very granular control, ensuring that only specific devices or applications can talk to each other, and only in very specific ways.
Third, these firewalls evolved to perform application-layer filtering. Instead of just looking at IP addresses and ports, they can analyze the actual applications running on top of communication protocols. This provides deeper security by distinguishing between normal operational commands and malicious activity that might be hidden inside legitimate-looking traffic. For example, a command to “read data” might be allowed, while a command to “change setpoint” from an unauthorized source would be blocked immediately.
Finally, OT firewalls now support high availability and redundancy features designed for industrial use. In environments like power grids, oil refineries, or manufacturing lines, even a momentary network disruption can have costly or dangerous consequences. Industrial firewalls are engineered to handle continuous uptime, support redundant hardware configurations, and tolerate the challenging physical conditions of plant environments, such as electrical noise, temperature extremes, or vibration.
In short, firewalls for industrial networks have matured far beyond their IT ancestors. They are now specialized security devices that combine traditional packet filtering with deep industrial protocol awareness, network segmentation, and resilience features. This evolution reflects the growing recognition that OT environments face distinct threats, and that protecting them requires tools specifically designed for the realities of industrial operations.
Configuration and Management Challenges in OT Environments
Managing firewalls in OT environments creates challenges. Industrial systems often need 24/7 availability, which means maintenance windows are scarce. Configuration changes require careful planning and testing. Firewall rule sets can become incredibly complex, and mistakes can block legitimate traffic or allow malicious activity through.
Another challenge involves keeping up with security updates and threat intelligence. Firewall effectiveness depends heavily on current threat signatures and properly configured rules. This ongoing maintenance requirement can strain resources.
Key Differences: Data Diode vs Firewall Security Capabilities
Data diodes operate on a deterministic security model where the hardware design makes certain attacks physically impossible. Firewalls implement rule-based protection requiring constant management.
The deterministic nature of data diodes means your security posture doesn’t deteriorate over time. Firewalls, on the other hand, rely on constant vigilance, updates, and adjustments.
Maintenance and Operational Requirements
Firewalls need regular updates, rule changes, and monitoring. Data diodes need minimal maintenance once deployed. Firewall management requires cybersecurity expertise; data diodes require more upfront network design work.
Performance and Operational Considerations
Data diodes excel in high-throughput scenarios and handle any IP-based protocol without modification. Firewalls introduce latency due to inspection and require protocol-specific support.
Operationally, firewalls enable remote access while data diodes eliminate it. Organizations must balance between absolute security and operational flexibility.
Data Diodes Regulatory Compliance
Data diodes align closely with critical infrastructure protection standards, offering simple, verifiable compliance. Firewalls can support compliance, too, but require continuous updates and detailed documentation.
Implementation Scenarios
Use data diodes for critical systems that can’t tolerate compromise, such as power generation or chemical processing. Use firewalls when bidirectional communication and remote access are essential, such as in manufacturing. A layered approach using both often makes the most sense.
Waterfall Security’s Unidirectional Security Gateway
Waterfall Security Solutions pioneered hardware-enforced unidirectional protection. Their Unidirectional Security Gateway advances data diode concepts with support for industrial protocols, secure file transfers, and solutions like HERA (Hardware-Enforced Remote Access).
Waterfall Security’s technology provides deterministic security guarantees while addressing practical deployment challenges in industrial networks. With proven deployments in power, oil and gas, water treatment, transportation, and more, Waterfall offers a reliable approach to OT cybersecurity.
Conclusion
When it comes to protecting Critical infrastructure, your choice between data diodes and firewalls does not have to be an either/or decision. While data diodes provide absolute protection through unidirectional communication and firewalls offer flexible, bidirectional connectivity with rule-based security, the most robust OT security strategies often combine both.
By adding hardware-enforced protection to segment critical networks, organizations can dramatically strengthen their security posture. This layered approach ensures that even if a firewall is compromised, the physical barrier provided by a data diode prevents threats from reaching your most sensitive systems. As cyber threats against OT continue to evolve, combining these technologies delivers resilience and safety for the future.
As cyber threats against OT continue to evolve, understanding these differences ensures resilience and safety for the future.