Facilities Cyber Security Solutions
Cybersecurity for building automation – Building automation systems range from safety-critical to reliability critical: elevator controls must be protected from cyber sabotage, heating, ventilation and air conditioning (HVAC) systems must run and we cannot afford misoperation of HVAC systems that leads to equipment damage and long-term outages.
Data Centers
Large data centers host the world's cloud systems. While information in the cloud is protected with IT-grade cybersecurity, Unidirectional technology provides engineering-grade protection for remote monitoring and remote access into critical systems including electric power, HVAC and physical security and access control systems.

Casinos
Rich targets for ransomware and other sabotage, casinos benefit from unidirectional protections for systems critical to operation, including escalators, elevators, HVAC systems and lighting.

Airports
Large airports are small cities. They have their own power and water systems, and some larger airports have internal transportation infrastructure. Just like physical airport security, cybersecurity is a top concern. Cyber threats to airport infrastructure are increasing dramatically, and regulators are introducing new demands to maintain an airport's operational resilience even during a cyber-attack. Protecting critical operational systems (baggage handling systems, SCADA systems, airport lighting controls, fuel management systems, etc.) requires hardware-enforced cyber protections that meet the challenges of today's attacks while addressing future unknown capabilities.

With Waterfall you get

Secure Remote Access
Waterfall’s HERA® , Hardware-Enforced Remote Access, provides the functionality of remote access, without the inherent risks and threats that come with network connectivity.

Real-time security monitoring
Real time visibility into networks and building automation security configurations through Unidirectional Gateways increases protection for critical systems, without creating connections, and the cyber risks that come with connections, into protected systems to gather security data.

Safe Equipment Monitoring
Enterprise-wide and visibility into equipment availability, new equipment issues and developing problems through Unidirectional Gateways enable safe and efficient prioritization and scheduling of maintenance activities.
Use cases
Remote Access
Hardware Enforced Remote Access (HERA® ) enables remote management, updates, and troubleshooting for OT networks, safely. When software-based secure remote access is too great a risk, HERA® ‘s hardware provides remote functionality without the risks of remote connectivity.
Equipment Monitoring
Unidirectional Gateways offer unbreachable protection to critical equipment, while replicating OPC servers, real-time databases, Syslog alerts, SNMP alerts and other critical performance indicators to enterprise systems and users, and external vendors and service providers.
Passenger Monitoring
Video feeds, turstile counters and other data is routinely replicated unidirectionally to IT networks to provide insights into passenger traffic patterns and bottlenecks, passenger safety issues and real-time rail / bus and shuttle scheduling.
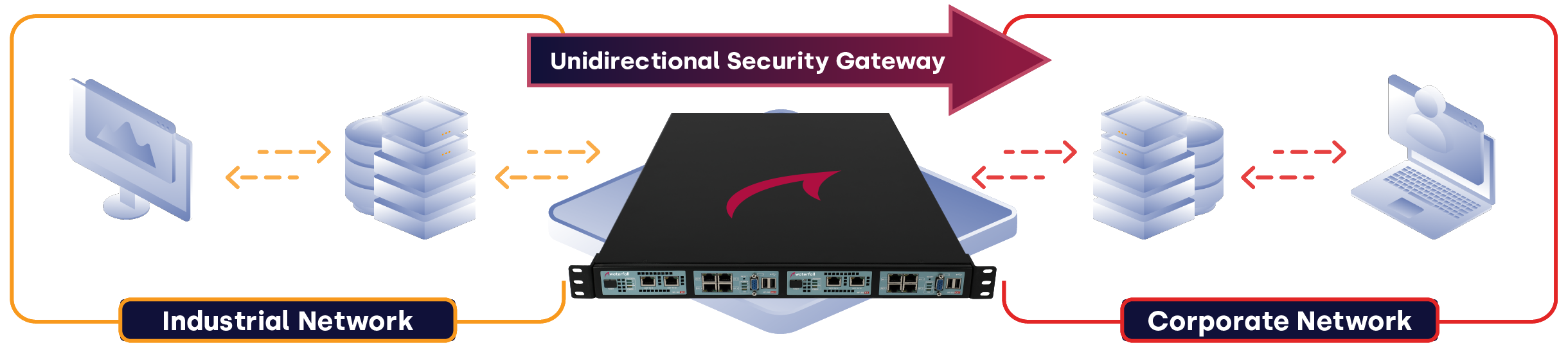
How it works

Connect
An industrial network safely to an IT network

Protect
The industrial network with hardware enforced technology

Replicate
Real-time operational servers to the enterprise IT network