Hardware-Enforced Secure Remote Access for OT Environments
HERA reinvents OT secure remote access with built-in physical protections to deliver unparalleled security for your critical systems.

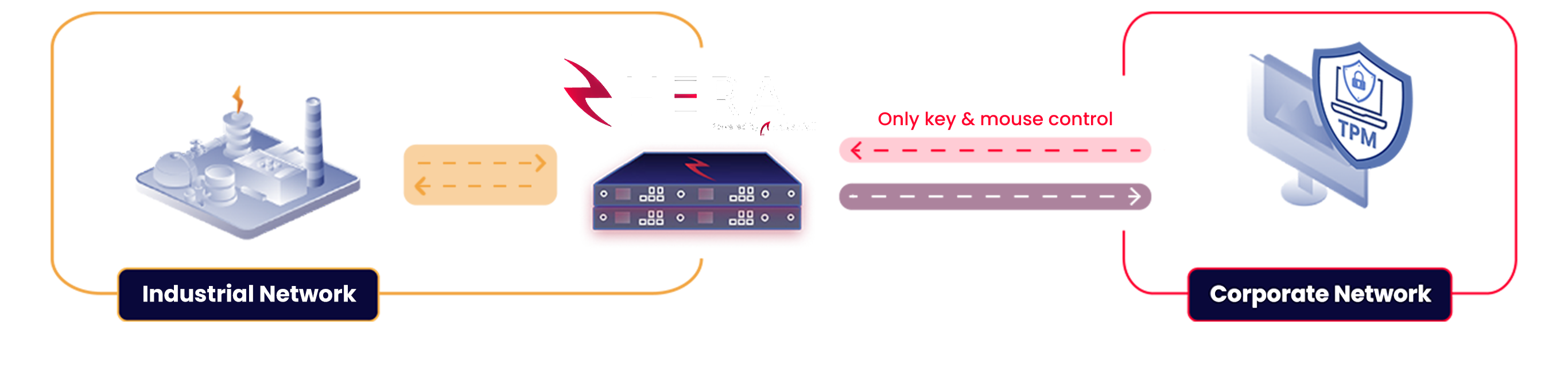
IT/OT Integration with Physical Segmentation
A physical defense that shields OT environments from all cyber threats while enabling seamless manageable remote access.
Full-Featured Remote Access
Experience fully secure remote access with everything you need in one solution.
Reliable & Safe
Battle-proven unidirectional technology that’s successfully protected OT environments globally since 2007.
Embedded Defense, Unparalleled Security
Physically Securing the OT perimeter
HERA® locks down your OT environments with dual best-in-class unidirectional gateways, eliminating risks of attacks propagating into the OT network.
Enhanced Protocol Isolation
Physically separate encrypted inbound and outbound channels enable strict protocol isolation, preventing Man-in-the-Middle attacks. Only mouse and keyboard inputs are sent from the client to the server.
Specialized Client-Side Software
Hardware-enforced Trusted Platform Module (TPM) technology secures key storage to block key theft attacks and uses message encryption to prevent client-side attacks. Binding hardware to the user and site ensures the strongest mufti-factor authentication.
Secure Remote Access with Fine-Grain Control
Session Recording

Gain comprehensive visibility and accountability through real-time session recording for all remote access activities. Every user interaction within the OT environment is logged, creating a detailed audit trail for compliance, forensic analysis, and security monitoring.
Session Moderation

Fine-Grain User Management

Zero Trust Controls

Implement zero-trust, time-based access to enhance security by verifying every access request. Grant access to specific users only during designated times or within predefined time windows, ensuring precise control and minimizing potential risks.
Logging & SIEM Reporting

Log and monitor detailed and extensive metrics within a dedicated monitoring system, providing a clear audit trail for every activity. Logs can also be seamlessly exported to SIEM tools for advanced analysis and security event management, ensuring comprehensive oversight.
Multi-Site Management

Easily manage multiple sites from a single interface. Oversee and control operations across various locations without the need for separate logins or interfaces.
Client-Side Software

Ensure secure connections with software that sits client-side, eliminating any risk from Man-in-the-Middle attacks