Cybersecurity For Hyundai Steel
Protecting Steel Casting Process From External Cyber Threats

Customer/ Partner:
Hyundai Steel.
Customer Requirement:
Enable safe operations monitoring, big data aggregation & analytics, quality optimization, and central monitoring of the continuous casting process.
Waterfall’s Unidirectional Solution:
Secures control process network perimeters from external threats with Unidirectional Security Gateways, enabling central access to operations status and production details, enabling enterprise-wide visibility and an advanced IIoT application platform.
The Modern Manufacturing Industry Is Facing An Increased Attack Surface
With the increased connectivity of digital devices inside a smart manufacturing plant comes a remarkable increase in attack surface. To avoid the costly turn-arounds, the modern, highly–connected manufacturing plant needs a solution to keep attackers out while simultaneously analyzing and aggregating data for plant optimization.

The challenge
Enable secure monitoring, data aggregation and analysis of continuous casting plant information while protecting safe and reliable operations. Enable centralized monitoring, visibility and IIoT applications while preventing remote cyber threats from entering the process network.

Waterfall solution
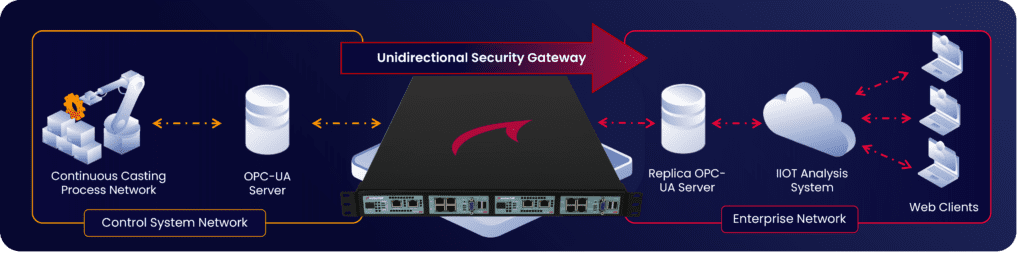
A Waterfall Unidirectional Security Gateway was installed between the control system and the enterprise network. Unidirectional Gateway software replicates OPCUA servers from the production network to enterprise network for use by centralized and cloudbased data aggregation, analysis, quality optimization, and predictive maintenance, platforms.
Results & benefits
Security: A Unidirectional Gateway provides strong assurance that no attack from the IT network can enter the process network. Visibility: Enterprise and IIoT applications monitor continuous casting process data in real-time. Central and cloud-based applications aggregate and analyze OPC-UA replica data. The replication process is transparent to these applications. Compliance: Unidirectional Gateways simplify compliance with enterprise security programs and with regional and global cyber security standards and regulations.
Theory of Operation
Click the digram to enlarge
Waterfall Security is the market leader for Unidirectional Gateway technology with installations at critical infrastructure sites across the globe. The enhanced level of protection provided by Waterfall’s Unidirectional Security Gateway technology is recognized as best practice by leading industry standards bodies and authorities such as NIST, ANSSI, NERC CIP, the ISA, the US DHS, ENISA and many more.
Global Cybersecurity Standards Recommend Unidirectional Security Gateways
Waterfall Unidirectional Security Gateways replace firewalls in industrial network environments, providing absolute protection to control systems and industrial control networks from attacks emanating from external lesstrusted networks. Waterfall Gateways contain both hardware and software components. The hardware is physically able to send information in only one direction. The software replicates servers and emulates devices. At Hyundai Steel, the gateway software produces an accurate, timely replica of a production OPC-UA server. Enterprise and cloud-based IIoT applications and users use the OPC-UA replica exclusively. Unidirectional Gateways enable control-system intrusion detection, vendor monitoring, industrial cloud services, and visibility into operations for modern enterprises and customers. Unidirectional Gateways replicate servers, emulate industrial devices and translate industrial data to cloud formats. Unidirectional Gateway technology represents a plug-and-play replacement for firewalls, without the vulnerabilities and maintenance issues that accompany firewall deployments. Replacing at least one layer of firewalls in a defense-in-depth architecture breaks the attack path from the Internet to critical systems.
Unidirectional Security Gateways Benefits:
![]() Safe, continuous monitoring of operations networks from IT-managed central platforms
Safe, continuous monitoring of operations networks from IT-managed central platforms
![]() Strong, physical protection for production processes, quality and personnel safety
Strong, physical protection for production processes, quality and personnel safety
![]() Safe remote supervision of changes to protected systems
Safe remote supervision of changes to protected systems
![]() Safe cloud vendor supply chain integration
Safe cloud vendor supply chain integration
![]() Central enterprise security and performance monitoring for OT networks and applications
Central enterprise security and performance monitoring for OT networks and applications
Share
Trending posts
Applying the New NCSC / CISA Guidance
IT/OT Cyber Theory: Espionage vs. Sabotage
Ships Re-Routed, Ships Run Aground
Stay up to date
Subscribe to our blog and receive insights straight to your inbox