Secure Remote Access: Everything You Need to Know in 2025
Securing remote access to operational technology (OT) networks requires specialized approaches that protect critical infrastructure while maintaining real-time performance. This guide covers the unique challenges, essential security layers, major risks, and key considerations for choosing OT remote access solutions that balance operational continuity with robust cybersecurity.
Waterfall team

What is Secure Remote Access and Why Does it Matter Today?
Secure remote access for OT (Operational Technology) networks represents one of the most critical cybersecurity challenges facing industrial organizations today. Unlike traditional IT environments, OT networks control physical processes in manufacturing plants, power grids, water treatment facilities, and other critical infrastructure. Secure remote access in these environments must balance operational continuity with stringent security requirements, ensuring that authorized personnel can monitor and maintain industrial systems without exposing them to cyber threats.
In OT environments, secure remote access solutions must address unique challenges that don’t exist in conventional IT networks. Industrial control systems often run legacy protocols and software that weren’t designed with modern security in mind. These systems require specialized secure remote access approaches that can protect SCADA systems, PLCs, and HMIs while maintaining the real-time performance requirements essential for safe operations. The stakes are particularly high because a security breach in OT networks can result in production shutdowns, safety incidents, or even physical damage to equipment and infrastructure.
The importance of secure remote access for OT networks has grown exponentially as industrial organizations embrace digital transformation and Industry 4.0 initiatives. Remote monitoring, predictive maintenance, and centralized operations management all depend on secure remote access capabilities. The COVID-19 pandemic further accelerated this need, forcing many industrial organizations to enable remote access for maintenance technicians, engineers, and operations personnel who previously worked exclusively on-site.
Modern secure remote access solutions for OT environments typically employ air-gapped architectures, dedicated secure gateways, and protocol-aware security controls. These systems create secure tunnels that allow authorized users to access OT networks without direct internet connectivity, often using jump servers or secure remote desktop solutions specifically designed for industrial environments. Advanced solutions incorporate OT-specific monitoring capabilities, protocol inspection, and integration with industrial security information and event management (SIEM) systems to provide comprehensive protection while enabling necessary remote operations.
How Secure Remote Access Actually Works
Secure remote access for OT networks operates through a multi-layered architecture designed to protect critical industrial systems while enabling authorized personnel to perform essential monitoring and maintenance tasks. The process begins with establishing a secure perimeter around OT assets, typically using dedicated secure gateways or jump servers that act as intermediaries between external users and sensitive industrial control systems. These secure remote access solutions create an isolated pathway that prevents direct internet connectivity to OT networks while maintaining operational functionality.
The authentication process in OT secure remote access systems is particularly robust, often requiring multi-factor authentication combined with role-based access controls specific to industrial environments. Users must first authenticate to the secure remote access gateway, which then validates their credentials against both IT identity systems and OT-specific authorization databases. Once authenticated, the system establishes encrypted tunnels using industrial-grade protocols that can handle the unique communication requirements of SCADA systems, PLCs, and other OT devices while maintaining the low-latency performance critical for real-time operations.
Data transmission in OT secure remote access solutions employs protocol-aware filtering and inspection capabilities that understand industrial communication standards like Modbus, DNP3, and OPC. The secure remote access system monitors all traffic flowing between remote users and OT devices, applying security policies that block unauthorized commands while allowing legitimate operational activities. Advanced solutions include session recording and audit capabilities that capture every action performed during remote sessions, providing complete visibility into who accessed which systems and what changes were made.
Modern OT secure remote access implementations often incorporate zero-trust principles specifically adapted for industrial environments. This means that every connection attempt is verified and validated, regardless of the user’s location or previous access history. The secure remote access system continuously monitors session behavior, device health, and network traffic patterns to detect anomalies that might indicate a security threat. When suspicious activity is detected, the system can automatically terminate sessions, alert security personnel, and initiate incident response procedures to protect critical OT infrastructure from potential cyber attacks.
The 5 Biggest Security Risks When Accessing Networks Remotely
1. Compromised Endpoints and Device Security
One of the most significant threats to secure remote access in OT environments comes from compromised endpoints used by remote workers. Personal devices, unmanaged laptops, or inadequately secured workstations can serve as entry points for malware that subsequently infiltrates industrial networks. In OT environments, this risk is particularly dangerous because infected devices can potentially disrupt critical infrastructure operations or provide attackers with persistent access to SCADA systems and industrial controls.
2. Man-in-the-Middle Attacks and Network Interception
Secure remote access connections are vulnerable to man-in-the-middle attacks, especially when users connect from unsecured public networks or compromised internet connections. For OT networks, these attacks can be catastrophic because intercepted communications might reveal sensitive operational data, system configurations, or real-time process information. Attackers who successfully position themselves between remote users and OT systems can potentially inject malicious commands or steal critical infrastructure intelligence.
3. Credential Theft and Authentication Bypass
Weak authentication mechanisms represent a fundamental vulnerability in secure remote access systems. Stolen credentials, password attacks, or authentication bypass techniques can grant unauthorized access to critical OT networks. In industrial environments, compromised credentials can allow attackers to manipulate production processes, disable safety systems, or access proprietary operational data. The challenge is compounded by the fact that many OT systems still rely on default passwords or shared accounts that are difficult to secure effectively.
4. Insider Threats and Privileged Access Abuse
Secure remote access systems can inadvertently enable insider threats, particularly when privileged users abuse their legitimate access rights. In OT environments, authorized personnel with remote access capabilities might intentionally or unintentionally cause operational disruptions, data theft, or safety incidents. The remote nature of access makes it more difficult to monitor user behavior and detect anomalous activities that might indicate malicious intent or compromised accounts.
5. Lateral Movement and Network Segmentation Failures
Once attackers gain initial access through compromised secure remote access connections, they often attempt lateral movement to expand their foothold within OT networks. Poor network segmentation, excessive user privileges, or inadequate monitoring can allow threats to spread from initial access points to critical industrial systems. In OT environments, this lateral movement can potentially impact multiple production lines, safety systems, or even entire facilities, making proper network isolation and access controls essential for maintaining operational security.
Essential Building Blocks of Effective Secure Remote Access Solutions
Building a robust secure remote access solution for OT networks requires integrating multiple security technologies and architectural components that work together to protect critical industrial infrastructure. Unlike traditional IT environments, OT secure remote access solutions must accommodate the unique requirements of industrial control systems while maintaining the stringent security standards necessary to protect operational technology from cyber threats. The following essential building blocks form the foundation of any effective secure remote access architecture designed for industrial environments, each serving a specific role in creating comprehensive protection for remote connectivity to critical OT assets.
Identity Verification: The Foundation of Secure Remote Access
Identity verification serves as the cornerstone of any secure remote access system, particularly in OT environments where unauthorized access can lead to catastrophic operational disruptions or safety incidents. In industrial networks, robust identity verification goes beyond traditional username and password combinations to incorporate multi-layered authentication mechanisms specifically designed for the high-stakes nature of operational technology. Effective identity verification for OT secure remote access must balance stringent security requirements with the operational realities of industrial environments, ensuring that authorized personnel can quickly access critical systems during emergencies while maintaining ironclad protection against unauthorized intrusion attempts.
Protecting the Connection: Encryption and Tunneling Technologies
Once identity verification establishes user authenticity, encryption and tunneling technologies become the critical defense mechanism that protects data transmission in secure remote access systems. In OT environments, these technologies must safeguard sensitive industrial communications while accommodating the unique protocols and real-time requirements of operational technology networks. Effective encryption and tunneling for OT secure remote access requires specialized approaches that can handle industrial communication standards like Modbus, DNP3, and OPC while maintaining the low-latency performance essential for safe and efficient industrial operations. The challenge lies in implementing robust encryption that protects against sophisticated cyber threats without compromising the deterministic communication patterns that many industrial control systems depend upon for reliable operation.
Securing Every Device: Endpoint Protection for Remote Access
Endpoint protection represents a critical vulnerability point in secure remote access architectures, as compromised devices can serve as launching pads for attacks against OT networks and industrial control systems. In operational technology environments, endpoint security takes on heightened importance because a single infected device connecting remotely to industrial networks can potentially disrupt entire production processes or compromise safety systems. Effective endpoint protection for OT secure remote access must address the diverse range of devices used by remote workers, from personal laptops and mobile devices to specialized industrial terminals and ruggedized field equipment. The challenge is implementing comprehensive endpoint security measures that can validate device health, detect malware, and enforce compliance policies without creating operational barriers that prevent authorized personnel from accessing critical OT systems when needed.
Managing Access Rights: Granular Control of Remote Resources
Access rights management forms the final layer of defense in secure remote access systems, determining precisely what resources, systems, and functions each authenticated user can access within OT networks. In industrial environments, granular access control becomes paramount because different personnel require varying levels of access to operational technology systems based on their roles, responsibilities, and operational requirements. Effective access rights management for OT secure remote access must implement role-based permissions that align with industrial hierarchies while maintaining the principle of least privilege to minimize potential attack surfaces. The complexity increases when considering that OT environments often require emergency access protocols, temporary elevated permissions for maintenance activities, and real-time access adjustments based on operational conditions, all while maintaining comprehensive audit trails and compliance with industrial security standards.
Real-World Examples: Secure Remote Access in Action
Power Generation and Grid Operations
Electric utilities worldwide rely on secure remote access solutions to monitor and control power generation facilities and distribution networks from centralized operations centers. During severe weather events or grid emergencies, operators use secure remote access to quickly assess system status, reroute power flows, and coordinate restoration efforts across multiple substations and generation plants. These OT secure remote access systems enable real-time monitoring of SCADA networks while maintaining strict isolation between corporate IT networks and critical power grid infrastructure, ensuring that remote operations personnel can respond to outages without exposing the electrical grid to cyber threats.
Manufacturing and Production Control
Global manufacturing companies implement secure remote access to enable engineers and technicians to troubleshoot production issues, perform predictive maintenance, and optimize manufacturing processes from remote locations. For example, automotive manufacturers use secure remote access solutions to allow headquarters engineering teams to remotely diagnose problems at plants worldwide, reducing downtime and travel costs while maintaining production quality. These systems provide encrypted connections to industrial control systems, enabling remote access to PLCs, HMIs, and manufacturing execution systems while preventing unauthorized access to sensitive production data and intellectual property.
Water Treatment and Municipal Infrastructure
Water treatment facilities and municipal utilities deploy secure remote access solutions to enable 24/7 monitoring and emergency response capabilities for critical infrastructure systems. Operations personnel can remotely monitor water quality parameters, adjust treatment processes, and respond to system alarms from off-site locations, ensuring continuous service delivery while maintaining cybersecurity. These OT secure remote access implementations often include redundant communication paths and fail-safe mechanisms that automatically secure systems if unauthorized access attempts are detected, protecting public health and safety infrastructure from potential cyber attacks.
Oil and Gas Pipeline Operations
Pipeline operators use secure remote access systems to monitor thousands of miles of pipeline infrastructure, compressor stations, and pumping facilities from centralized control rooms. Field technicians can securely connect to remote terminal units (RTUs) and pipeline monitoring systems to perform maintenance, collect operational data, and respond to emergencies without physically traveling to remote locations. These secure remote access solutions incorporate specialized protocols for industrial communications while providing the real-time data transmission capabilities essential for safe pipeline operations and environmental protection.
Evaluating Secure Remote Access Solutions: What to Look For
Which OT remote access solution is right for you? It depends on the sensitivity of your OT/physical process, on your risk tolerance, and on your assessment of credible threats. In Waterfall’s upcoming webinar, we look at the landscape of available OT remote access solutions, how they compare risk-wise, and what a decision tree for choosing between the alternatives looks like.
One core assumption: we are trying to prevent cyber attacks pivoting from the Internet (possibly via intervening IT and other networks) into sensitive OT networks and sabotaging physical operations.
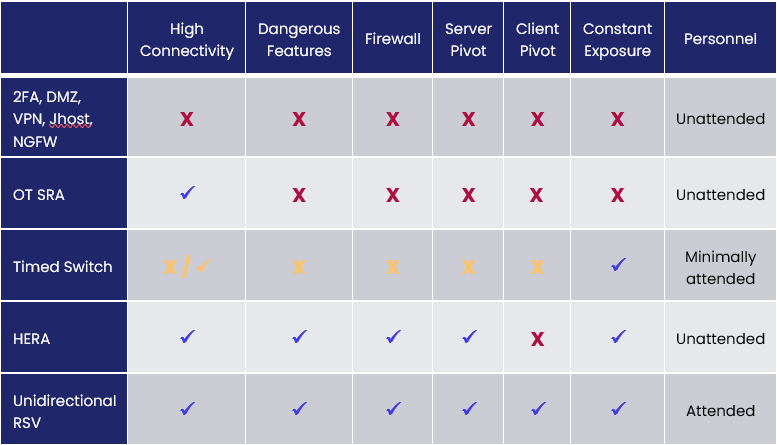
Different types of solutions include:
- 2FA, DMZ, VPN, Jhost, NGFW – this is a conventional IT/OT remote access system, such as the system described as the minimum acceptable for NERC CIP Medium Impact sites, including (more or less) two-factor authentication, a demilitarized zone “network between networks,” a virtual private network, a jump host, and a next-gen firewall.
- OT SRA – is a typical OT “secure” remote access solution that works roughly like Microsoft Teams – there is a client in the OT network and it reaches out through an IT/OT firewall to connect to remote laptops and other clients, either by contacting those clients directly or by reaching into a cloud service or other server to rendezvous with clients.
- Timed switch – a timed hardware switch that temporarily connects / disconnects a conventional type (1) or (2) software-based remote access solution to an IT network or the Internet. The timed switch is normally in a disconnected state and enables temporary remote connectivity infrequently.
- Hardware-Enforced Remote Access – Waterfall’s HERA, which consists of cooperating inbound and outbound gateways designed to prevent attacks pivoting from the Internet into OT systems.
- Unidirectional remote screen view technology – tech that lets the remote user “look but not touch” and requires an engineer or other human operator in the protected OT network to cooperate with the remote expert providing remote support.
Features & Characteristics of Remote Access Solutions
To compare risks in these solutions, we look at a number of features & characteristics:
- High connectivity – CISA and other authorities recently requested that high-consequence sites stop using VPNs for remote access, in large part because VPNs very often provide more connectivity into IT and OT networks than is needed and is wise.
- Dangerous features – many “secure” remote access solutions have a myriad of features including dangerous ones such as file transfers (of potentially malicious files) and clipboard cut-and-paste operations (of potentially large attack scripts).
- Firewalled – most “secure” remote access solutions demand a firewall at the IT/OT interface. Firewalls have a role inside OT networks and inside IT networks but are often not strong enough to defend a consequence boundary – when OT and IT networks have dramatically different worst-case consequences of compromise.
- Server pivot – most “secure” remote access solutions have fairly constant IP addresses. They are in a sense “sitting ducks” for any adversary who cares to test them, any time that adversary cares to test them – for zero days, for unpatched known vulnerabilities, for misconfigurations and so on. And once these remote access servers are compromised, the attacker can pivot through the compromised remote access equipment, using the compromised equipment to attack more valuable assets deeper into the OT network.
- Client pivot – most remote access solutions can be misused by attackers if he remote workstation or laptop is taken over. Two-factor authentication makes this harder, but not impossible, since 2FA is also software with vulnerabilities, both known and zero-day. Attackers thus are able to pivot through a compromised remote endpoint into the protected OT network.
- Constant exposure – most remote access solutions are “always on” – constantly exposed to attacks from compromised external networks, such as IT networks and the Internet.
- Personnel – most remote access solutions are designed for unattended operation, meaning that no OT personnel need be present at or internally connected to remote sites, such as substations, pump stations, lift stations, compressor stations or other remote installations. Attended operation systems that work only if there are local personnel present to help them along tend to be more secure, but those personnel are not always available.
How do we use these characteristics to choose between the options?
Well, we need to understand our needs and especially the criticality of our physical operations. A key question: what is the worst consequence possible due to a credible attack scenario? The question has three key parts:
- Worst possible consequence – what is the worst that can happen if compromised computers either fail to function correctly, or more often are deliberately made to function maliciously. And beware – many risk programs have blind spots, such as bricked control equipment. What happens if the bad guys get in and load dummy firmware into most of our 10-year-old PLCs, damaging them so thoroughly that it is now impossible to reload them with correct firmware? Where do we get spares to replace these components when the manufacturer no longer produces this equipment?
- Credible attacks – in the spectrum of possible attacks (see Waterfall’s report on the Top 20 Cyber Attacks on Industrial Control Systems), which attack scenarios and consequences do we deem credible threats, given the defenses we have already deployed and the remote access systems we are considering, and which consequences and attacks do we not believe will be realized in our network or in any similar networks, any time soon?
- Acceptable consequences – which credible consequences, due to credible attacks on our systems, do we deem acceptable vs. unacceptable?
All this and more, in greater detail, with industry-specific examples, can be learned by watching our past webinar ‘Building a Game Plan for OT Remote Access‘.
Key Takeaways: Securing Remote Access in a Changing World
As operational technology environments embrace digital transformation, securing remote access to critical industrial systems has become both essential and increasingly complex. Unlike traditional IT networks, OT environments control physical processes where security breaches can lead to production shutdowns, safety incidents, or infrastructure damage.
Security Requires Multiple Layers
Effective OT remote access security cannot rely on any single control. The most resilient implementations combine robust identity verification, encrypted communications, endpoint protection, and granular access controls. This multi-layered approach addresses the five major threat categories: compromised endpoints, man-in-the-middle attacks, credential theft, insider threats, and lateral movement opportunities.
Balance Security with Operations
The greatest challenge lies in balancing stringent cybersecurity requirements with operational realities. Industrial control systems require deterministic communication and real-time performance that cannot be compromised. Effective solutions must natively understand industrial protocols, maintain air-gapped architectures, and provide the reliability that critical infrastructure demands.
The Future is Zero-Trust for OT
Traditional perimeter-based security is inadequate for modern OT environments. The shift toward zero-trust architectures – where every connection is verified and continuously monitored – represents the future of OT cybersecurity. However, implementation must carefully consider industrial workflows and emergency access requirements to avoid operational disruptions.
Preparing for Tomorrow
As organizations continue embracing remote operations capabilities, comprehensive OT remote access security becomes a strategic enabler rather than a barrier. Organizations that invest in protocol-aware protection, air-gapped architectures, and scalable solutions today will be better positioned to capitalize on future opportunities while maintaining security and reliability.
The path forward requires viewing OT remote access security as an enabling capability that allows safe adoption of operational flexibility and efficiency. With the right foundation, remote access becomes a competitive advantage in the digital transformation of industrial operations.
About the author
Waterfall team
FAQs About Secure Remote Access
What makes OT remote access different from regular IT remote access?
OT networks control physical processes in manufacturing plants, power grids, and critical infrastructure where security breaches can cause production shutdowns, safety incidents, or equipment damage. Unlike IT systems, OT networks require specialized security solutions that understand industrial protocols (like Modbus and DNP3), maintain air-gapped architectures, and provide real-time performance without compromising operational safety.
What are the biggest security risks when accessing OT networks remotely?
The five major risks are: compromised endpoints that can inject malware into industrial systems, man-in-the-middle attacks that intercept critical operational data, credential theft enabling unauthorized system access, insider threats from privileged users abusing access rights, and lateral movement where attackers spread from initial access points to critical industrial controls.
What should I look for when choosing an OT remote access solution?
Prioritize solutions that natively support industrial protocols, maintain network air-gaps through secure gateways or jump servers, provide real-time performance for time-sensitive operations, offer comprehensive audit trails for compliance, and can scale with your infrastructure. The platform should integrate with existing security tools while preserving the strict separation between IT and OT networks.
Share
Trending posts
Cross Domain Solutions Explained
Risks, Rules & Gaps: The Latest on NIS2 and CRA
Stay up to date
Subscribe to our blog and receive insights straight to your inbox